BK101
Knowledge Base
Internet - World Wide Web
Internet Privacy - Internet Safety - Child Safety - Internet Education - Safe Browsing - Privacy
Data Protection - Internet Scams - Open Internet - Info - Censorship - Consumer Safety - Spam
Learning how to Safely and Effectively use the Internet. Learning how to Effectively and Efficiently Navigate the Internet.
 Warning: When visiting other websites
be very careful what you click on because
some software downloads are very dangerous to your computer, so be
absolutely sure what you are downloading. Read the '.exe
file name by either mousing over the link and reading
the bottom browser bar or by reading the file name in the download box.
Even search engines can link directly to websites that have viruses,
malicious software, key stroke recorders, parasites, tracking cookies and
many other vulnerabilities and threats, so be very aware of the websites
you are visiting. And don't click on links in e-mails too, unless you know
for sure, because they could also take you to fraudulent and threatening
websites. Don't ever click on Links in
social networks unless you are absolutely positive.
Disclosure.
Warning: When visiting other websites
be very careful what you click on because
some software downloads are very dangerous to your computer, so be
absolutely sure what you are downloading. Read the '.exe
file name by either mousing over the link and reading
the bottom browser bar or by reading the file name in the download box.
Even search engines can link directly to websites that have viruses,
malicious software, key stroke recorders, parasites, tracking cookies and
many other vulnerabilities and threats, so be very aware of the websites
you are visiting. And don't click on links in e-mails too, unless you know
for sure, because they could also take you to fraudulent and threatening
websites. Don't ever click on Links in
social networks unless you are absolutely positive.
Disclosure.
Internet Network Explained
Internet is an interconnected network of computers all over the world that connects people and information 24 hours a day. The internet is a computer network consisting of a worldwide network of servers that use the TCP/IP Network Protocols to facilitate data transmission and exchange and to communicate between networks and devices. It is a network of networks that consists of private, public, academic, business, and government networks of local to global scope, linked by a broad array of electronic, wireless, and optical networking technologies. The Internet carries a vast range of information resources and services, such as the inter-linked hypertext documents and applications of the World Wide Web (WWW), electronic mail, telephony, and file sharing.
Of course the internet is a lot more than its definition. Simply trying to define what the internet is, is almost impossible. It's the biggest and the most important human advancement ever. Second only to the advancements in computers, and right before that, the advancements in language and the written word, which was our first defining moment. And because of this early Writing System, we learned to communicate much more effectively, and convey a lot more knowledge and information. And now with computers, and the Internet, and the digitizing of language, we are now transmitting more knowledge and information then any other time in our history. So just like when we look back at see how language changed our world, future generations will look back at the internet and see how the internet transformed our world. A world that will be greatly improved.
The internet is a lot bigger then you think, literally, figuratively and philosophically. But instead of listing the thousands of benefits that are coming from this internet network, I want to talk briefly about an interesting similarity. It seems that the internet is just a natural process of life. Just like the internet, life wants to branch out and make connections. Similar to the root systems Mycorrhiza found in Mushrooms located in Michigan’s Upper Peninsula. And also like the Quaking Aspen's, or Pando Trees, in Utah and Colorado. But life not only branches out and makes more connections, life also lives Symbiotically, and learns how to adapt. If not, that life form eventually dies, as history has proven. And when that happens, then you become a fossil for future life to look back on and say, "Hey, I wonder what happened to these creatures, they seemed to have had a brain, but I guess they never learned how to use it? I will write more about the internet, but for now, I like analyzing the similarities between life and the internet, it reminds me of the similarities between the human brain and computers. The internet is a human's way of mimicking biology. Human intelligence is advancing faster then any other time in human history, and Artificial Intelligence is just another tool that we have created to enhance our abilities and increase our potential. (The first internet message was sent from UCLA's campus on Oct. 29, 1969).
The Wood Wide Web, are Plants Inter-Connected by a Subterranean Fungal Network?
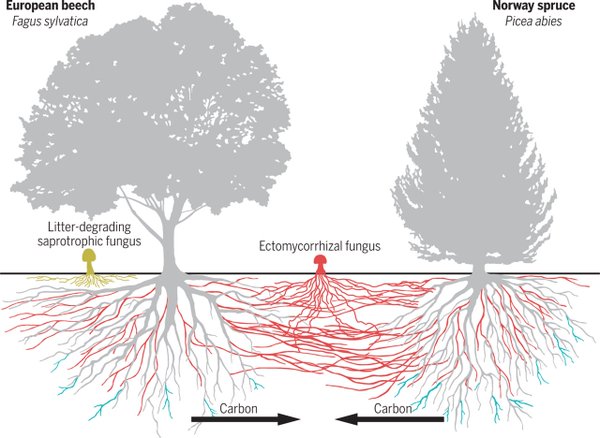 Mycorrhizal
Network are underground hyphal networks created by mycorrhizal
fungi
that connect individual plants together and transfer water, carbon,
nitrogen, and other nutrients and minerals. The formation of these
networks is context dependent, and can be influenced by soil fertility,
resource availability, host or myco-symbiont genotype, disturbance and seasonal variation.
Humongous Fungus.
Mycorrhizal
Network are underground hyphal networks created by mycorrhizal
fungi
that connect individual plants together and transfer water, carbon,
nitrogen, and other nutrients and minerals. The formation of these
networks is context dependent, and can be influenced by soil fertility,
resource availability, host or myco-symbiont genotype, disturbance and seasonal variation.
Humongous Fungus.
Clonal Colony is a group of genetically identical individuals, such as plants, fungi, or bacteria, that have grown in a given location, all originating vegetatively, not sexually, from a single ancestor. In plants, an individual in such a population is referred to as a ramet. Pando tree (wiki).
Rhizoid are protuberances that extend from the lower epidermal cells of bryophytes and algae. They are similar in structure and function to the root hairs of vascular land plants. Similar structures are formed by some fungi. Rhizoids may be unicellular or multicellular. Roots are multicellular organs composed of multiple tissues that collectively carry out a common function.
Matrix - Internet of Things - Weaving
Populus Tremuloides often propagates through its roots to form large groves originating from a shared system of rhizomes.
Internet is Human Intelligence in Action
Internet Infrastructure
A Brief History of the Internet - First Website, First Meme (youtube).
 Hyperlinks link
documents and
information.
Synapses in the human
brain are connections between neurons
through which "information" flows from one
neuron to another.
Some hypertext hyperlinks can be bidirectional: they can be
followed in two directions, so both ends act as anchors and as
targets. More complex arrangements exist, such as many-to-many
links.
Hyperlinks link
documents and
information.
Synapses in the human
brain are connections between neurons
through which "information" flows from one
neuron to another.
Some hypertext hyperlinks can be bidirectional: they can be
followed in two directions, so both ends act as anchors and as
targets. More complex arrangements exist, such as many-to-many
links.Anchor Text is the link label, link text, or link title is the visible, clickable text in a hyperlink.
Artificial Neural Network - DNA
Neurobiology is the study of cells of the nervous system and the organization of these cells into functional circuits that process information and mediate behavior. It is a subdiscipline of both biology and neuroscience.
Intranet is a private network accessible only to an organization's staff.
 Extranet is a website that allows controlled access to
partners, vendors and suppliers or an authorized set of customers –
normally to a subset of the information accessible from an organization's
intranet. An extranet is similar to a DMZ in that it provides access to
needed services for authorised parties, without granting access to an
organization's entire network. An extranet is a private network
organization. Historically the term was occasionally also used in the
sense of two organizations sharing their internal networks over a
VPN.
Extranet is a website that allows controlled access to
partners, vendors and suppliers or an authorized set of customers –
normally to a subset of the information accessible from an organization's
intranet. An extranet is similar to a DMZ in that it provides access to
needed services for authorised parties, without granting access to an
organization's entire network. An extranet is a private network
organization. Historically the term was occasionally also used in the
sense of two organizations sharing their internal networks over a
VPN.LAN, or Local Area Network, is a computer network that interconnects computers within a limited area such as a residence, school, laboratory, university campus or office building and has its network equipment and interconnects locally managed. By contrast, a wide area network (WAN), not only covers a larger geographic distance, but also generally involves leased telecommunication circuits or Internet links. Wi-Fi.
Internet Protocol is the principal communications protocol in the Internet protocol suite for relaying datagrams across network boundaries. Its routing function enables internetworking, and essentially establishes the Internet.
Internet Protocol Suite is the conceptual model and set of communications protocols used on the Internet and similar computer networks. It is commonly known as TCP/IP because the foundational protocols in the suite are the Transmission Control Protocol (TCP) and the Internet Protocol (IP).
Making the internet more energy efficient through systemic optimization using smart, error-correcting data chip circuits, which they refined to be 10 times less energy consumptive.
List of TCP and UDP Port Numbers used by protocols of the transport layer of the Internet protocol suite for the establishment of host-to-host connectivity. Originally, port numbers were used by the Network Control Program (NCP) in the ARPANET for which two ports were required for half-duplex transmission. Later, the Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP) needed only one port for full-duplex, bidirectional traffic. The even-numbered ports were not used, and this resulted in some even numbers in the well-known port number range being unassigned. The Stream Control Transmission Protocol (SCTP) and the Datagram Congestion Control Protocol (DCCP) also use port numbers. They usually use port numbers that match the services of the corresponding TCP or UDP implementation, if they exist. The Internet Assigned Numbers Authority (IANA) is responsible for maintaining the official assignments of port numbers for specific uses. However, many unofficial uses of both well-known and registered port numbers occur in practice. Similarly many of the official assignments refer to protocols that were never or are no longer in common use. This article lists port numbers and their associated protocols that have experienced significant uptake.
 Internet Connection using Cellphone Towers
Internet Connection using Cellphone TowersCell Reception
Wi-Fi Jetpack (RSSI signal) Mobile Hotspot
Weboost Signal Booster
Directional Wi-Fi Antenna
Wi-Fi Warnings
"How could we become so connected and yet be so disconnected at the same time?"
Social Networks
Search Engines
Internet Searching Tips
Human Search Engine
Language Translations
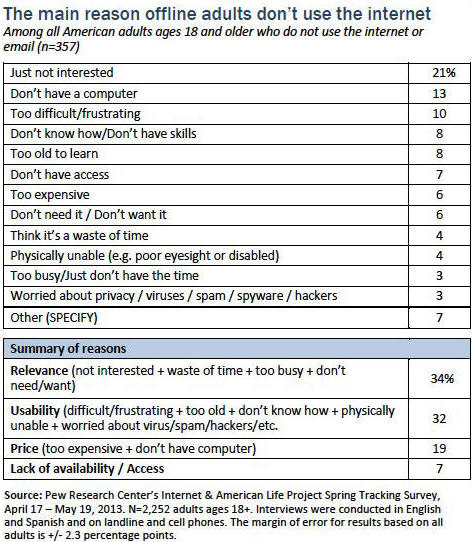
The main reason why most people don't use the internet is because most people do not understand the value, the importance or the potential that the internet offers. So when the other 3/4's of the worlds population does get access, they should know better on how to use the internet, as well as know why, when and where to access the internet.
Los Alguiens - El Internet (ORIGINAL VERSION) (Internet Song on youtube) - Lyrics Translated: If you want to download a song, download it from internet, If you want a girlfriend, look for her in internet. You want to host a party, host it on internet, If you want to read the news, do it on internet, The internet, the internet, the internet, the internet, the internet, the internet, the internet, the internet.
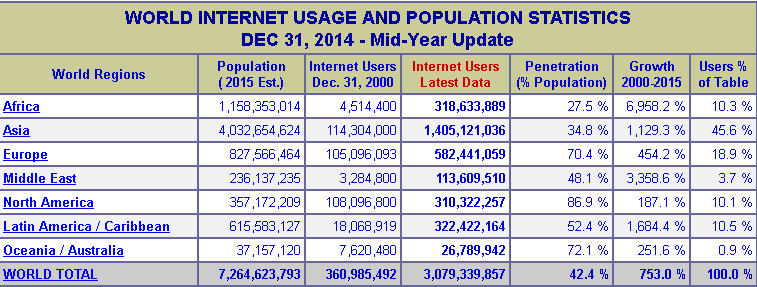 4 Billion People Still Don't Have Internet Access in 2016, and
most of the 3 billion who do have Internet Access, are not
using the internet effectively or efficiently. Just
having access does not say anything.
60 percent of the world isn’t online. There is more mobile phone coverage.
4 Billion People Still Don't Have Internet Access in 2016, and
most of the 3 billion who do have Internet Access, are not
using the internet effectively or efficiently. Just
having access does not say anything.
60 percent of the world isn’t online. There is more mobile phone coverage.
List of Countries by Number of Internet Users (wiki)
Internet Use Demographics (PDF)
How Many Computers?
44% of offline adults have asked a friend or family member to look something up or complete a task on the internet for them.
50 million people in America don't log on. - Laptops for Senior Citizens
Pew Internet - Internet Society - Project Link
F the Internet (youtube) Funny video about this women's idea what the internet is.
What people are Searching for on the Internet
 Of course people will never know the true details of what
search
engines know about what people are looking for on the internet.
Or will people know what information Google is selling, or know
who is buying this information, or know what certain people plan
to do with that information? So what do our internet
searches say about us? What does your Search History say about
you? What does your Browser History say about you?
Of course people will never know the true details of what
search
engines know about what people are looking for on the internet.
Or will people know what information Google is selling, or know
who is buying this information, or know what certain people plan
to do with that information? So what do our internet
searches say about us? What does your Search History say about
you? What does your Browser History say about you? Google will display their pretty trends, but they will not share the most important information. So people will only see the stupid stuff that people search for on Google. The amount of Things that happen in one day are enormous.
2001 Top Internet Queries: 1. Nostradamus 2. CNN 3. World Trade Center 4. Harry Potter 5. Anthrax 6. Windows XP 7. Osama Bin Laden 8. Audiogalaxy 9. Taliban 10. Loft Story 11. Afghanistan 12. Nimba 13. American Airlines 14. American Flag. 15. Aaliyah. 16. FBI 17. Kazaa 18. Lord of the Rings 19. Jennifer Lopez 20. Xbox.
The 2013 list of top-trending searches (global) included Nelson Mandela, Paul Walker, iPhone 5s, Cory Monteith, Harlem Shake, Boston Marathon, Royal Baby, Samsung Galaxy s4, PlayStation 4 and North Korea.
Most searched beauty question: How to get rid of acne. Most searched dog question: Why do dogs eat grass? Top-trending memes search: Tim Howard memes. Top-trending natural events search: Hurricane Arthur. Most searched places on Google maps: Wal-Mart. Top-trending podcast search: Serial. Top-trending book search: Boy, Snow, Bird.
Top internet searches are most related to what's happening in the media, and since the media is mostly irrelevant, that means people are not learning as much as they should be from the internet, which is extremely alarming. There is nothing more damaging to a person then the belief that they are learning enough in order to be accurately aware of themselves and the world around them. This is what is happening in our education system, as well as the media, and now the internet. And this false sense of learning enough, is demonstrated throughout the world in the form of violence, wars, crimes and mental disorders. So your biggest mass murderers are not just the people who control the media, your largest mass murders are the people who control education and what is being taught in schools. But try to explain that to people is almost impossible, considering the amount of damage that has been afflicted on them from our media outlets and from our schools. You can't speak or understand a language that you never heard of. And this language is called intelligence, where knowledge and information is clearly understood. Teach the language of intelligence and you will eventually solve every problem in the world.
Google indexes no more than 16 percent of the surface Web and misses all of the Deep Web. Any given search turns up just 0.03 percent of the information that exists online (one in 3,000 pages) Much of the Deep Web’s unindexed material lies in mundane databases such as LexisNexis or the rolls of the U.S. Patent Office.
Wikipedia Statistics
"The internet connects more then just computers, the internet connects minds. And when people finally do understand this ability, the saying "the word travels fast" will be an understatement."
Web at 25
"Most people don't understand the internet, they don't realize the potential of the internet, or what it means to be connected to the worlds most valuable knowledge and information."
"The world is moving so fast these days that the man who says it can't be done is generally interrupted by someone doing it."
Disclaimer - Discloser - Confidentiality
Basic Knowledge 101.com does not share our users personal information. But that does not mean that your personal information is secure because we cannot control other websites privacy policies and what they do with your personal information. So we encourage our members and site visitors to be aware of the privacy policies of the other websites that we link too. When a new browser window opens we encourage our users to be aware of the privacy statements of each website that collects personally identifiable information. Please be aware that Basic Knowledge 101.com can not be responsible for Links that no longer point to the original site on which it was intended because the Domain name, or ULR, was sold or high jacked by the people where the domain name was registered. We apologize and will remove the link as soon as we are notified. If a site we link to is found to be fraudulent in any way we will remove it and no longer link to that website. If a website that we link to does not want us to link to them we will remove it and no longer link to that site.
Editor's Warning - Discretion Advised - Arbitration Clause
Personal Information - Confidentiality - Consent
BK101 does not indorse every opinion or every action that other people do. Nor does BK101 indorse every opinion or every action that BK101 does because mistakes happen. BK101 likes to confirm the accuracy of opinions and actions through the process of intelligent consensuses. But even then, this will still not guarantee that you wont learn anything new, which would ultimately change your opinion, or change your action.
BK101 does not agree with everything that is portrayed in Documentaries, Movies, TV Shows or any other media outlets. BK101 assimilates the most logical parts of information and puts them together to form an understanding. Then BK101 writes down these understandings so that this information can be shared with others. Every person must learn how to recognize what information is accurate and valuable. So what is your procedure for filtering and assimilating information? Media Literacy.
Disclaimer is a statement intended to specify or delimit the scope of rights and obligations that may be exercised and enforced by parties in a legally recognized relationship. In contrast to other terms for legally operative language, the term disclaimer usually implies situations that involve some level of uncertainty, waiver, or risk.
For Entertainment Purposes Only is the denial, refusal, or rejection of a right, power, or responsibility. A disclaimer is a defensive measure, used generally with the purpose of protection from unwanted claims or liability. A disclaimer of Warranty, which is provided for in the Uniform Commercial Code, limits a warranty in the sale of goods. Negligence.
Disclosure is the act of making something evident, to make visible. To make known to the public information that can be misinterpreted. To make vulnerabilities known.
Full Disclosure is the acknowledgement of possible conflicts of interest in one's work.
Fine Print - Adhesion Contract - Contract Law - Non Disclosure Agreement (keep things private).
Non-Disclosure Agreement or Confidentiality Agreement is a legal contract between at least two parties that outlines confidential material, knowledge, or information that the parties wish to share with one another for certain purposes, but wish to restrict access to or by third parties. It is a contract through which the parties agree not to disclose information covered by the agreement. An NDA creates a confidential relationship between the parties to protect any type of confidential and proprietary information or trade secrets. As such, an NDA protects non-public business information.
Hush Money - Gag Order - Suppression - Censorship - Freedom of Speech - Whistleblower
Non-Disparagement Clause is when a former employee gives up the right to sue the employer in exchange for compensation and also agrees not to make negative statements that cause real damage to the other party or the publication of false and injurious statements that are derogatory of another's property, business, or product. The answers to these questions depend on how your state and your local courts and judges defines the term.
Attorney–Client Privilege (loopholes for wealthy criminals)
Computer Security Full Disclosure are flaws in software that can be abused to cause unintended behavior, these flaws are called vulnerabilities.
Terms of Service are rules by which one must agree to abide in order to use a service. Terms of service can also be merely a disclaimer, especially regarding the use of websites.
Release Form is a legal instrument that acts to terminate any legal liability between the releasor and the releasee(s), signed by the releasor.
Waiver is the voluntary relinquishment or surrender of some known right or privilege. A waiver is a legally binding provision where either party in a contract agrees to voluntarily forfeit a claim without the other party being liable. Waivers can either be in written form or some form of action. Examples of waivers include the waiving of parental rights, waiving liability, tangible goods waivers, and waiver for grounds of inadmissibility or unacceptability as a consequence of not being admissible or deserving to be admitted. Waiving of Parental Rights: In cases involving the custody of a child, a biological parent may choose to waive their legal rights as a parent, making that person ineligible to make determinations regarding the child's upbringing. This also allows a guardian who is not a biological parent to attempt to assert their right over a child through actions such as adoption. Waivers of Liability: Before participating in an activity that could lead to injury or death, a person may be required to sign a waiver as a form of expressed consent to the risks that exist, due to the inherent nature of the activity. This waiver would release the company facilitating the activity from liability should the participant be injured or killed during his participation. Such waivers may be used prior to participating in extreme sports, such as BMX racing, or other activities, such as skydiving. Waivers and Tangible Goods: In the case of most tangible goods or personal property, a person may waive the right to continue to make a claim on the item. This can apply to goods that are sold to a new buyer or donated to a particular entity. A transfer of vehicle ownership functions as a waiver of any claim to the item by the seller, and it gives the right to the buyer as the new owner. Exemption.
Do you have to make a disclosure even when you're not misleading anyone? Almost all information can be misinterpreted. But if you intentionally present information that can be misinterpreted, then that's propaganda, those are when disclosures are absolutely necessary. But you never see disclosures in the news, on TV, in books or in the movies. Even if you do see disclosures they too can be misleading, so the disclosure needs a disclosure. And you wonder why learning information literacy and media literacy are extremely important.
Privacy Policy is a statement or a legal document (in privacy law) that discloses some or all of the ways a party gathers, uses, discloses, and manages a customer or client's data. It fulfills a legal requirement to protect a customer or client's privacy. Personal information can be anything that can be used to identify an individual, not limited to the person's name, address, date of birth, marital status, contact information, ID issue and expiry date, financial records, credit information, medical history, where one travels, and intentions to acquire goods and services. In the case of a business it is often a statement that declares a party's policy on how it collects, stores, and releases personal information it collects. It informs the client what specific information is collected, and whether it is kept confidential, shared with partners, or sold to other firms or enterprises. Privacy policies typically represent a broader, more generalized treatment, as opposed to data use statements, which tend to be more detailed and specific. The exact contents of a certain privacy policy will depend upon the applicable law and may need to address requirements across geographical boundaries and legal jurisdictions. Most countries have their own legislation and guidelines of who is covered, what information can be collected, and what it can be used for. In general, data protection laws in Europe cover the private sector as well as the public sector. Their privacy laws apply not only to government operations but also to private enterprises and commercial transactions.
Licensing Agreements are a set of terms under which one party can use property owned by another party. The property involved in a licensing agreement can be real, personal or intellectual, but licensing agreements are most often used for intellectual property.
Software License is a legal instrument of contract law, with or without printed material) governing the use or redistribution of software.
Free Software License is a notice that grants the recipient of a piece of software extensive rights to modify and redistribute that software. These actions are usually prohibited by copyright law, but the rights-holder (usually the author) of a piece of software can remove these restrictions by accompanying the software with a software license which grants the recipient these rights. Software using such a license is free software (or free and open source software) as conferred by the copyright holder. Free software licenses are applied to software in source code as also binary object code form, as the copyright law recognizes both forms.
End-User License Agreement is the Contract between the licensor and purchaser, establishing the purchaser's right to use the software. The license may define ways under which the copy can be used, in addition to the automatic rights of the buyer including the first sale doctrine and 17 U.S.C. § 117 (freedom to use, archive, re-sale, and backup). Many form contracts are only contained in digital form, and only presented to a user as a click-through where the user must "accept". As the user may not see the agreement until after he or she has already purchased the software, these documents may be contracts of adhesion. Software companies often make special agreements with large businesses and government entities that include support Contracts and specially drafted warranties, which provides assurance by one party to the other party that specific facts or conditions are true or will happen. This factual guarantee may be enforced regardless of materiality which allows for a legal remedy if that promise is not true or followed.
Clickwrap or clickthrough agreement is a digital prompt that offers individuals the opportunity to accept or decline a digital media policy, which outlines specific rules for the use of social media at Interior.
Fair Use - Permissions
BK101 contains copyrighted material, the use of which has not always been specifically authorized by the copyright owner. We are making such material available in our efforts to advance understanding of issues of humanitarian significance. We believe this constitutes a 'fair use' of any such copyrighted material as provided for in section 107 of the US Copyright Law. In accordance with Title 17 U.S.C. Section 107, the material on this site is distributed without profit to those who have expressed a prior interest in receiving the included information for research and educational purposes. If you wish to use copyrighted material from this site for purposes of your own that go beyond 'fair use', you must obtain permission from the copyright owner. Bk101 does not claim ownership of any Intellectual Property that was not personally created.
Humanitarian is marked by humanistic values and devotion to human welfare. Someone devoted to the promotion of human welfare and to social reforms. An advocate of the principles of humanism and someone who is concerned with the interests and the welfare of humans. Assistance - Defender.
Social Service - Big 5 Needs - Humanism - Civics - Free Speech
Welfare is something that aids or promotes well-being. A satisfied state of being happy and healthy and prosperous.
Creative Commons-License Attribution 4.0 International (CC BY 4.0)
Share — copy and redistribute the material in any medium or format.
Adapt — remix, transform, and build upon the material for any purpose, even commercially.
Free to Copy does not mean that something is free. All information has a responsibility. Share with accountability.
You must give appropriate credit to the millions of people who shared their work and knowledge that helped the human race survive and thrive. We must give thanks to the printing press that was built over 500 years ago. And we also must give thanks to the millions of our ancestors who helped preserve language and helped pass it on, for without language, humans would have never survived. But even with all the technological advances that humans have made in the last 200 years, we are just beginning to understand how extremely important language and communication is. Human civilization is at a turning point. When all humans finally realize the power of knowledge, then people will stop falling victim to the lack of knowledge, and the ignorance that is destroying each other and destroying our only home.
Internet Education
Get Net Wise
Seniors Guide to using Computers and Software
Child Technology Education
Technology Addiction
Tek Mom
Inter Lingo, Acronyms, Jargon and Text Message Shorthand
Internet 101
Internet Basic Knowledge
Internet History begins with the development of electronic computers in the 1950s.
Advanced Research Projects Agency Network (ARPANET)
Net Smartz
Computer Definitions
Printout Definitions
Computer Knowledge
Keeping Kids Safe on The Internet
 Internet
Safety is the knowledge of maximizing the user's personal
safety and security risks to private information and property associated
with using the internet, and the self-protection from computer crime in general.
Oversight.
Internet
Safety is the knowledge of maximizing the user's personal
safety and security risks to private information and property associated
with using the internet, and the self-protection from computer crime in general.
Oversight.Childre's Online Privacy Protection Act is a United States federal law, located at 15 U.S.C. §§ 6501–6506 (Pub.L. 105–277, 112 Stat. 2681-728, enacted October 21, 1998). The act, effective April 21, 2000, applies to the online collection of personal information by persons or entities under U.S. jurisdiction about children under 13 years of age including children outside the U.S., if the company is U.S.-based. It details what a website operator must include in a privacy policy, when and how to seek verifiable consent from a parent or guardian, and what responsibilities an operator has to protect children's privacy and safety online including restrictions on the marketing of those under 13. While children under 13 can legally give out personal information with their parents' permission, many websites—particularly social media sites, but also other sites that collect most personal info—disallow children under 13 from using their services altogether due to the cost and work involved in complying with the law.
Child Online Protection Act was a law in the United States of America, passed in 1998 with the declared purpose of restricting access by minors to any material defined as harmful to such minors on the Internet. The law, however, never took effect, as three separate rounds of litigation led to a permanent injunction against the law in 2009. The law was part of a series of efforts by US lawmakers legislating over Internet pornography. Parts of the earlier and much broader Communications Decency Act had been struck down as unconstitutional by the Supreme Court in 1997 (Reno v. ACLU); COPA was a direct response to that decision, narrowing the range of material covered. COPA only limits commercial speech and only affects providers based within the United States. COPA required all commercial distributors of "material harmful to minors" to restrict their sites from access by minors. "Material harmful to minors" was defined as material that by "contemporary community standards" was judged to appeal to the "prurient interest" and that showed sexual acts or nudity (including female breasts). This is a much broader standard than obscenity.
Children's Ombudsman is a public authority in various countries charged with the protection and promotion of the rights of children and young people, either in society at large, or in specific categories such as children in contact with the care system. The agencies usually have a substantial degree of independence from the executive, and generally operate as specialised ombudsman offices or national human rights institutions, dealing with individual complaints, intervening with other public authorities, conducting research, and – where their mandate permits them to engage in advocacy – generally promoting children's rights in public policy, law and practice. The first children's commissioner was established in Norway in 1981. The creation of such institutions has been promoted by the United Nations Committee on the Rights of the Child, and, from 1990 onwards, by the Council of Europe. (children's commissioner, youth commissioner, child advocate, children's commission, youth ombudsman or equivalent body).
Stay Safe Online.org
On Guard Online.gov
Safe Browsing Tools
Enough
Internet Safety 101
Online Family Norton
Safe Kids.com
Safe Kids.org
Google Safety Tips
Kidoz Kid Safe Internet Browser
Connect Safely.org
Wired Safety.org
The World Wide Web is one of the greatest tools ever invented and literally the biggest library in the world. But the Internet is not a safe and secure place so be aware of the dangers and take some time to educate yourself on How to be Safer on the Internet. Whatever your age your personal information can be exploited and used against you, so be careful.
There is a strong privacy law that protects your cable viewing habits, but there is no such law that protects records of what you buy online or is there a law that protects information that is collected by other services such as social networks or advertising networks.
FCC Rules offer protections against your mobile phone company selling the location data it has on you from tracking your cell phone all over town and beyond, but at the same time you are not protected under these same rules given by the USA Patriot Act.
Bullying - Trolls
101 East: Web of Hate (youtube)
Cyber-Bullying is a form of bullying or harassment using electronic forms of contact.
Stop Bullying - Bully Knowledge - Crime Help (bullies)
Critics - Social Network Comments
Troll is a person who sows discord on the Internet by starting arguments or upsetting people, by posting inflammatory, extraneous, or off-topic messages in an online community (such as a newsgroup, forum, chat room, or blog) with the intent of provoking readers into an emotional response or of otherwise disrupting normal, on-topic discussion, often for the troll's amusement. Patent Troll - Trolling is what the Media does sometimes.
Imposters - Scammers - Sextortion
Apps: Stop it Cyber Bully
Stalking Amanda Todd : The Man in the Shadows (youtube)
The Fifth Estate (youtube 40:52)
Internet Searching Tips
PC Problem Solving
Technology is Just Another Tool
Information Sources
What did I Learn from the Internet
Human Search Engine
Online Education
Family Relationships
Censorship
Media Literacy
Child Development
Bad TV
The Greatest Tool for Internet Safety will always be Knowledge.
Spying on your child is not recommended. Only when all other methods of Communication have failed, and only if you believe that your child may be in danger, should you even try to attempt to violate your child's privacy, because you could easily make the situation worse. All parents need to continually educate themselves and keep up with today's information and knowledge. And let your child know that you are both responsible for each others actions.
You don't Know Everything - Relationships
Social Network Monitoring is just another word for Spying. If you want to know a person you have to talk to that person and have an open and honest conversation with them. Just listening in on someone's conversations, or watching them from a distance, and then judging them, or exploiting that information, without the decency of a fair and open trial, that is not just insane and insultingly ignorant, it is very dangerous. The damage that could come from these types of errors could be catastrophic. Spying is not a productive process for learning, it is flawed and vulnerable. You create more problems then you solve.
Make sure all computers are well-positioned so they cannot be pulled over by inquisitive children. Also make sure that cables are dressed and secured properly to avoid being tripped on.
Social Network Dangers
Assange talks about Facebook, called Facebook the "most appalling spying machine that has ever been invented." Face Book is the world's most comprehensive database about people, their relationships, their names, their addresses, their locations, their communications with each other, their relatives, all sitting within the United States, all accessible to U.S. intelligence. And ten years later, Cambridge Analytica was just another reminder that your information is still being sold.
Social Network Dangers - Social Network Comments - Critics
Facebook and the CIA - Facebook is tracking you whether you use it or not. Even if you've never signed up for Facebook or have logged out of your account, the social networking company is likely tracking your virtual movements — and it doesn't offer any way for you to opt out. Facebook doesn't curb hate speech in developing countries, where misinformation and hate speech can fuel real-world attacks.
Facebook is a good Social Network but it does have dangers. Facebook is not a secure website. It has hundreds of vulnerabilities and sometimes when using Facebook it does more harm then good. Facebook is not a BK101 indorsed social network. I do use it, but only sparingly, and I definitely don't share a lot info or comments. So please use it wisely. Be safe. Be aware. Propaganda and Fake News.
Facebook FTC 5 Billion Settlement is a Joke. Years of privacy practices in violation and forbidden user data collection of a previous order does not correspond to the harm done or rewards reaped. The investigation was rushed and incomplete. No charges or consequences and executives get immunity. Oversight is toothless and changes nothing, and endorses Facebook’s continued monetization of mass surveillance.
Global Disinformation Order. Evidence of organized social media manipulation campaigns which have taken place in 70 countries, up from 48 countries in 2018 and 28 countries in 2017. In each country, there is at least one political party or government agency using social media to shape public attitudes domestically. Government actors are using social media to manufacture consensus, automate suppression, and undermine trust in the liberal international order. Leveraging social media to shape public opinion, set political agendas, and propagate ideas. Weaponization of social media. Deceiving perceived enemies and influencing public opinion.
Social Network Scams and Vulnerabilities - Imposters
Privacy Concerns with Social Networking Services (wiki)
Social Network Safety - Chat Room Dangers
Social Media Etiquette - Morals
Internet Addiction
Kids Growing up Online (PBS) - DVD
Social Network Knowledge and Information
Internet Security Alliance
Dunbar Number is a suggested cognitive limit to the number of people with whom one can maintain stable social relationships. These are relationships in which an individual knows who each person is and how each person relates to every other person.
Fraud - Scams
 Fraud is deliberate deception to secure unfair or
unlawful gain, or to
deprive a victim of a legal right. Fraud itself can
be a civil wrong.
The remedies for fraud may include rescission (i.e., reversal) of a
fraudulently obtained agreement or transaction, the recovery of a monetary
award to compensate for the harm caused, punitive damages to punish or
deter the misconduct, and possibly others. Throughout the United States
fraud charges can be misdemeanors or
felonies depending on the amount of
loss involved. High value fraud can also trigger additional penalties. For
example, in California, losses of $500,000 or more will result in an extra
two, three, or five years in prison in addition to the regular penalty for
the fraud. Although elements may vary by jurisdiction and the specific
allegations made by a plaintiff who files a lawsuit that alleged fraud,
typical elements of a fraud case in the United States are that: Somebody
misrepresents a material fact in order to obtain action or forbearance by
another person; The other person relies upon the misrepresentation; and
The other person suffers injury as a result of the act or forbearance
taken in reliance upon the misrepresentation. To establish a civil claim
of fraud, most jurisdictions in the United States require that each
element of a fraud claim be pleaded with particularity and be proved by a
preponderance of the evidence. The U.S. government's 2006 fraud review
concluded that fraud is a significantly under-reported crime, and while
various agencies and organizations were attempting to tackle the issue,
greater co-operation was needed to achieve a real impact in the public
sector. The scale of the problem pointed to the need for a small but
high-powered body to bring together the numerous counter-fraud initiatives
that existed. The measure of damages in fraud cases is normally computed
using one of two rules: The "benefit of bargain" rule, which allows for
recovery of damages in the amount of the difference between the value of
the property had it been as represented and its actual value;
Out-of-pocket loss, which allows for the recovery of damages in the amount
of the difference between the value of what was given and the value of
what was received. Negligence.
Fraud is deliberate deception to secure unfair or
unlawful gain, or to
deprive a victim of a legal right. Fraud itself can
be a civil wrong.
The remedies for fraud may include rescission (i.e., reversal) of a
fraudulently obtained agreement or transaction, the recovery of a monetary
award to compensate for the harm caused, punitive damages to punish or
deter the misconduct, and possibly others. Throughout the United States
fraud charges can be misdemeanors or
felonies depending on the amount of
loss involved. High value fraud can also trigger additional penalties. For
example, in California, losses of $500,000 or more will result in an extra
two, three, or five years in prison in addition to the regular penalty for
the fraud. Although elements may vary by jurisdiction and the specific
allegations made by a plaintiff who files a lawsuit that alleged fraud,
typical elements of a fraud case in the United States are that: Somebody
misrepresents a material fact in order to obtain action or forbearance by
another person; The other person relies upon the misrepresentation; and
The other person suffers injury as a result of the act or forbearance
taken in reliance upon the misrepresentation. To establish a civil claim
of fraud, most jurisdictions in the United States require that each
element of a fraud claim be pleaded with particularity and be proved by a
preponderance of the evidence. The U.S. government's 2006 fraud review
concluded that fraud is a significantly under-reported crime, and while
various agencies and organizations were attempting to tackle the issue,
greater co-operation was needed to achieve a real impact in the public
sector. The scale of the problem pointed to the need for a small but
high-powered body to bring together the numerous counter-fraud initiatives
that existed. The measure of damages in fraud cases is normally computed
using one of two rules: The "benefit of bargain" rule, which allows for
recovery of damages in the amount of the difference between the value of
the property had it been as represented and its actual value;
Out-of-pocket loss, which allows for the recovery of damages in the amount
of the difference between the value of what was given and the value of
what was received. Negligence. Mail Fraud and Wire Fraud is any fraudulent scheme to intentionally deprive another of property or honest services via mail or wire communication. It has been a federal crime in the United States since 1872. Lying.
Ponzi Scheme - Confidence Trick - Phone Scams - False Advertising - Fine Print
False Pretenses is when a thief intentionally misrepresents past and present facts which the thief knows to be false, in order to defraud a person and obtain their money, goods, services or property. But if a thief makes a statement about something that they mistakenly believe to be untrue, there is no false representation, the thief just tried to lie but they failed.
FBI Scam Alerts - Watch out for bogus IRS agents, fake offers from tech support, and faux beaus or fake friends.
Scam Busters - Victims of Fraud Help - Watch Dogs
Fight Fraud - Fraud is a multi-billion dollar criminal industry, costing Americans more than the combined annual spending of many countries around the world. Fight Fraud in Connecticut - Crime Help Websites.
How to Report Fraud - Whistle Blowers
FBI Crime Reporting - Department of Justice
Internet Crime Complaint Center
Federal Trade Commission click on Consumer Protection.
Report Spam and Unsolicited E-Mails - Phone Fraud
Contact your States Attorney General
Travel Scams & Fraudulent Travel Deals - Vacation Rentals Scams and Complaints
Corporate Crimes - Healthcare Fraud - Food Fraud
Computer Crime is crime that involves a computer and a network. The computer may have been used in the commission of a crime, or it may be the target.
Internet Security Alliance - Computer Viruses
Information Protection Tools - Privacy Rights
Misappropriation is the unauthorized use of another's name, likeness, or identity without that person's permission, resulting in harm to that person.
Remember that the internet is not the only place where you can be scammed and have your identity stolen. Be cautious of suspicious phone calls, suspicious letters in the US mail and suspicious e-mails.
CAN-SPAM Act: A Compliance Guide for Business - CAN-SPAM Act of 2003 (wiki)
"The first principle is that you must not fool yourself -- and you are the easiest person to fool." (Richard Feynman)
Government Accountability
Better Business Bureau mission is to focus on advancing marketplace trust. The Better Business Bureau is not affiliated with any governmental agency. Businesses that affiliate with the BBB and adhere to its standards do so through industry self-regulation. To avoid bias, the BBB's policy is to refrain from recommending or endorsing any specific business, product or service. The organization has been the subject of controversy, particularly related to the allegation of giving higher ratings to businesses that pay a membership fee. bbb.org.
Consumer Protection
 Consumer Protection is a group of laws and
organizations designed to ensure the rights of
consumers as well as fair trade,
competition and accurate information in the marketplace. The laws are
designed to prevent the businesses that engage in
fraud or specified
unfair practices from
gaining an advantage over competitors
or consumers of a certain product or goods. They may also provide
additional protection for those most vulnerable in society. Consumer
protection laws are a form of government regulation that aim to protect
the rights of consumers. For example, a government may require businesses
to disclose detailed information about products—particularly in areas
where safety or
public health is an issue, such as food.
Consumer protection is linked to the idea of consumer rights and to the
formation of consumer organizations, which helps consumers make better
choices in the marketplace and get help with consumer complaints. Other
organizations that promote consumer protection include government
organizations and self-regulating business organizations such as consumer
protection agencies and organizations, the Federal Trade Commission in
America and Better Business Bureaus in America, Canada, England, etc. A
consumer is defined as someone who acquires goods or
services for direct
use or ownership rather than for resale or use in production and
manufacturing. Consumer interests can also serve consumers, consistent
with economic efficiency, but this topic is treated in competition law.
Consumer protection can also be asserted via non-government organizations
and individuals as consumer activism.
Consumer Protection is a group of laws and
organizations designed to ensure the rights of
consumers as well as fair trade,
competition and accurate information in the marketplace. The laws are
designed to prevent the businesses that engage in
fraud or specified
unfair practices from
gaining an advantage over competitors
or consumers of a certain product or goods. They may also provide
additional protection for those most vulnerable in society. Consumer
protection laws are a form of government regulation that aim to protect
the rights of consumers. For example, a government may require businesses
to disclose detailed information about products—particularly in areas
where safety or
public health is an issue, such as food.
Consumer protection is linked to the idea of consumer rights and to the
formation of consumer organizations, which helps consumers make better
choices in the marketplace and get help with consumer complaints. Other
organizations that promote consumer protection include government
organizations and self-regulating business organizations such as consumer
protection agencies and organizations, the Federal Trade Commission in
America and Better Business Bureaus in America, Canada, England, etc. A
consumer is defined as someone who acquires goods or
services for direct
use or ownership rather than for resale or use in production and
manufacturing. Consumer interests can also serve consumers, consistent
with economic efficiency, but this topic is treated in competition law.
Consumer protection can also be asserted via non-government organizations
and individuals as consumer activism. Consumer Dangers - Public Interest Research Groups - Online Buying Tips
Consumer Product Safety (gov) - Product Consumer Safety - Children
Consumer Action - Injuries from Window Blinds Send Two Children to the Emergency Department Every Day.
Consumer Watchdog focuses on insurance, health care, political reform, privacy and energy. consumerwatchdog.org.
Dangerous Goods are solids, liquids, or gases that can harm people, other living organisms, property, or the environment.
Consumer Education is the preparation of an individual to be capable of making informed decisions when it comes to purchasing products in a consumer culture. It generally covers various consumer goods and services, prices, what the consumer can expect, standard trade practices, etc. While consumer education can help consumers to make more informed decisions, some researchers have found that its effects can drop off over time, suggesting the need for continual education. New dimensions of consumer education are also beginning to emerge as people become more aware of the need for ethical consumerism and sustainable consumer behaviour in our increasingly globalized society.
Drug Warnings - Ways that People Die
Consumer Complaint Form for Ct. (PDF)
Consumer Complaints - Top 10 Consumer Complaints for 2014
Consumer Protection - Consumer Safety
U.S. Consumer Product Safety Commission
Safer Products - Consumer Affairs
Comparitech research's, tests, reviews and compares consumer tech products and services so you can make a more informed decision before you buy. Technology News.
National Consumers League
National Association of Consumer Advocates
Safer Chemicals - Green Science Policy
Consumer Info - Consumer Lab
Lead, if ingested or inhaled, its compounds are poisonous to animals and humans. Lead is a neurotoxin that accumulates both in soft tissues and the bones, damaging the nervous system and causing brain disorders. Excessive lead also causes blood disorders in mammals. Lead poisoning has been documented since ancient Rome, ancient Greece, and ancient China.
Water Pollution - Air Pollution - Soil Pollution - Food Safety
Phthalate are used in a wide range of common products, and are released into the environment. high doses have been shown to change hormone levels and cause birth defects.
Toxins (hazardous chemicals)
Perfectly Safe - One Step Ahead
Recalls - National Institute of Environmental Health Sciences
US won't seek recall of 56 million Takata air bag inflators. At least 25 people have been killed worldwide by Takata inflators and more than 300 have been injured. Problems with the company's products touched off the largest string of automotive recalls in U.S. history with around 50 million inflators recalled. About 100 million are being recalled worldwide. The decision announced Thursday involves newer inflators that contain a moisture-absorbing chemical. It means that millions of drivers will never know if they have Takata inflators in their vehicles, nor will they be repaired unless problems surface. It also means that up to 19 auto companies will avoid the huge expense of additional recalls. Takata had used the volatile chemical ammonium nitrate to create a small explosion to inflate air bags in a crash. But it was discovered that the chemical can deteriorate over time when exposed to high heat and humidity. It can explode with too much force, blowing apart a metal canister and hurling shrapnel into drivers and passengers. In most cases they won't fail for at least 25 years, well beyond the life cycle of most vehicles, he said. But in extreme heat in South Florida, limited tests showed failure was possible in 14-23 years.
American Chemistry - Consumer Info - E Opinions
Educational Toys and Games that Teach
Green Products - Physical Health News
Mental Health News - Lawyers, Court Information and Legal Help
Government Agencies - Trigger Warnings
Nearly 700 Children Have Perished In Hot Cars Since 1998.
Quality Control - Safety Engineering
According to The Internet Crime Complaint Center victims of Internet-related crimes lost $559 million in 2009, which is more because not all crimes are reported. The mission of most Social Networks like Facebook, is to get you to share as much information as possible so it can be shared with advertisers. Playing some of those free online games is one way to get people to share information. A few times a year Facebook puts your privacy settings back to a default setting, which essentially makes all of your information to be made public. And on top of that, your security is only as good as your friend's security. So if your friend is hacked you are at risk. Plus 40 percent of all Facebook profiles are fake, so please know your friends. Facebook has not been able to screen all of its ads either. Some ads have Malicious Code Embedded in them. And be absolutely sure what you are downloading because some antivirus software is actually a virus. Facebook reported that hackers using stolen username and password credentials try to break into at least 600,000 accounts every day. More Tech News.
Protecting the Internet Information Highway
 Net
Neutrality is the principle that Internet service providers should
treat all transmission of data over the Internet
equally and
not discriminate or charge differently based on
user, content, website, platform, application, type of equipment, or
method of communication.
When net neutrality is required, Internet service providers (ISPs) may not
intentionally block, slow down, or charge money for specific online
content. Conversely, without net neutrality regulations, ISPs may
prioritize certain types of traffic, meter others, or potentially
block
traffic from specific services, while charging consumers for various tiers of service.
Net
Neutrality is the principle that Internet service providers should
treat all transmission of data over the Internet
equally and
not discriminate or charge differently based on
user, content, website, platform, application, type of equipment, or
method of communication.
When net neutrality is required, Internet service providers (ISPs) may not
intentionally block, slow down, or charge money for specific online
content. Conversely, without net neutrality regulations, ISPs may
prioritize certain types of traffic, meter others, or potentially
block
traffic from specific services, while charging consumers for various tiers of service.
Go FCC Yourself.com - Keep Title II Net Neutrality Rules Strong. Protect Net Neutrality. No censorship and no deliberate slowing down of Data. Speed and accuracy is extremely important. (click on express). State officials have moved to keep net neutrality rules in place on their turf. Governors in six states — New Jersey, New York, Montana, Rhode Island, Vermont and Hawaii — have signed executive orders upholding net neutrality, and three – Washington, Vermont and Oregon — have enacted legislation that does so. In January, attorneys general in 22 states and the District of Columbia filed a protective petition for review of the order. Save the Internet.
Access is the right to enter and obtain and to make use of and to take advantage of a shared resource, such as Knowledge and Information. To obtain or retrieve Knowledge and Information from a storage device, like from a network computer. Access in computer science is the operation of reading or writing stored information.
Net Competition
Internet Innovation
Center for Democracy and Technology
Internet Freedom
Info War Monitor
Open Net
Internet Association is committed to promoting policies that protect the internet’s future. We are continuously updating so stay with us and check back for more.
Unused Airways - Transmission Space
White Spaces in radio are different frequencies for specific uses, and in most cases license the rights to broadcast over these frequencies. This frequency allocation process creates a bandplan, which for technical reasons assigns white space between used radio bands or channels to avoid interference. In this case, while the frequencies are unused, they have been specifically assigned for a purpose, such as a guard band. Most commonly however, these white spaces exist naturally between used channels, since assigning nearby transmissions to immediately adjacent channels will cause destructive interference to both. In addition to white space assigned for technical reasons, there is also unused radio spectrum which has either never been used, or is becoming free as a result of technical changes. In particular, the switchover to digital television frees up large areas between about 50 MHz and 700 MHz. This is because digital transmissions can be packed into adjacent channels, while analog ones cannot. This means that the band can be "compressed" into fewer channels, while still allowing for more transmissions. In the United States, the abandoned television frequencies are primarily in the upper UHF "700-megahertz" band, covering TV channels 52 to 69 (698 to 806 MHz). U.S. television and its white spaces will continue to exist in UHF frequencies, as well as VHF frequencies for which mobile users and white-space devices require larger antennas. In the rest of the world, the abandoned television channels are VHF, and the resulting large VHF white spaces are being reallocated for the worldwide (except the U.S.) digital radio standard DAB and DAB+, and DMB.
Free the TV White Space - Free the Airwaves (youtube) Video
Free the Airwaves - FCC White Space Rules - White Space - White Noise
Free-space Optical Communication is an optical communication technology that uses light propagating in free space to wirelessly transmit data for telecommunications or computer networking. "Free space" means air, outer space, vacuum, or something similar. This contrasts with using solids such as optical fiber cable or an optical transmission line. The technology is useful where the physical connections are impractical due to high costs or other considerations.
Freedom Tower - Free Network Foundation
Ad Busters - Scan Eye - Outernet - Lantern
Hacker - Hakerspaces - Can You Hack It? (video)
Li-Fi - EMF - Satellite Internet Access
FSO uses visible or infrared light to wirelessly transmit data through open air as opposed to using cables.
Improving Internet with Mid-Wavelength Infrared
High-Speed, Affordable, and Accessible Broadband
LTE telecommunication is a standard for high-speed wireless communication for mobile phones and data terminals. It is based on the GSM/EDGE and UMTS/HSPA network technologies, increasing the capacity and speed using a different radio interface together with core network improvements.
Affordable High-Speed Broadband for All Americans (youtube)
Lifeline Program for Low-Income Consumers (affordable internet access)
Google Fiber Connecting Public Housing at Gigabit Speeds
Connect Home
List of Countries by Internet Connection Speeds (wiki)
How to Connect to the internet when access is Limited
Mesh Networking is a network topology in which each node relays data for the network. All mesh nodes cooperate in the distribution of data in the network.
Wireless Mesh Network is a communications network made up of radio nodes organized in a mesh topology. It is also a form of wireless ad hoc network. Wireless mesh networks often consist of mesh clients, mesh routers and gateways. The mesh clients are often laptops, cell phones and other wireless devices while the mesh routers forward traffic to and from the gateways which may, but need not, be connected to the Internet. The coverage area of the radio nodes working as a single network is sometimes called a mesh cloud. Access to this mesh cloud is dependent on the radio nodes working in harmony with each other to create a radio network. A mesh network is reliable and offers redundancy. When one node can no longer operate, the rest of the nodes can still communicate with each other, directly or through one or more intermediate nodes. Wireless mesh networks can self form and self heal. Wireless mesh networks can be implemented with various wireless technologies including 802.11, 802.15, 802.16, cellular technologies and need not be restricted to any one technology or protocol.
Channel Bonding is a computer networking arrangement in which two or more network interfaces on a host computer are combined for redundancy or increased throughput. Channel bonding is differentiated from load balancing in that load balancing divides traffic between network interfaces on per network socket (OSI model layer 4) basis, while channel bonding implies a division of traffic between physical interfaces at a lower level, either per packet (OSI model Layer 3) or a data link (OSI model Layer 2) basis.
OSI Model Open Systems Interconnection Model is when a layer serves the layer above it and is served by the layer below it. For example, a layer that provides error-free communications across a network provides the path needed by applications above it, while it calls the next lower layer to send and receive packets that comprise the contents of that path. Two instances at the same layer are visualized as connected by a horizontal connection in that layer.
Load Balancing in computing improves the distribution of workloads across multiple computing resources, such as computers, a computer cluster, network links, central processing units, or disk drives. Load balancing aims to optimize resource use, maximize throughput, minimize response time, and avoid overload of any single resource. Using multiple components with load balancing instead of a single component may increase reliability and availability through redundancy. Load balancing usually involves dedicated software or hardware, such as a multilayer switch or a Domain Name System server process. Load balancing differs from channel bonding in that load balancing divides traffic between network interfaces on a network socket (OSI model layer 4) basis, while channel bonding implies a division of traffic between physical interfaces at a lower level, either per packet (OSI model Layer 3) or on a data link (OSI model Layer 2) basis with a protocol like shortest path bridging.
Connection Types
H.R. 2454: Aaron’s Law Act of 2013
Was Aaron Swartz Murdered?
Guerilla Open Access Manifesto
Activism
UK Parliament calls for internet to be classified as a Public Utility
Vodafone Communications
Named Data Networking: Instead of numbers, use names. Focus not on the locations of things, but on the things themselves by retrieving information from the nearest computer that has it, rather than wait to get it from a heavily-trafficked centralized servers.
From a Point to Point system to a Peer to Peer system.
The Case for a Decentralized Internet: Tamas Kocsis (video and text)
Decentralized Computing is the allocation of resources, both hardware and software, to each individual workstation, or office location. In contrast, centralized computing exists when the majority of functions are carried out, or obtained from a remote centralized location. Decentralized computing is a trend in modern-day business environments. This is the opposite of centralized computing, which was prevalent during the early days of computers. A decentralized computer system has many benefits over a conventional centralized network. Desktop computers have advanced so rapidly, that their potential performance far exceeds the requirements of most business applications. This results in most desktop computers remaining idle (in relation to their full potential). A decentralized system can use the potential of these systems to maximize efficiency. However, it is debatable whether these networks increase overall effectiveness. All computers have to be updated individually with new software, unlike a centralised computer system. Decentralised systems still enable file sharing and all computers can share peripherals such as printers and scanners as well as modems, allowing all the computers in the network to connect to the internet. A collection of decentralized computers systems are components of a larger computer network, held together by local stations of equal importance and capability. These systems are capable of running independently of each other.
Bitcoin (decentralized currency)
European Parliament has copyright protection law Article 13
Decentralized Network 42 is a decentralized peer-to-peer network built using VPNs and software/hardware BGP routers. While other darknets try to establish anonymity for their participants, that is not what dn42 aims for. It is a network to explore routing technologies used in the Internet and tries to establish direct non-NAT-ed connections between the members. The network is not fully meshed. dn42 uses mostly tunnels instead of physical links between the individual networks. Each participant is connected to one or more other participants. Over the VPN or the physical links, BGP is used for inter AS routing. While OSPF is the most commonly used protocol for intra AS routing, each participant is free to choose any other IGP for his AS.
E band waveguide s the range of radio frequencies from 60 GHz to 90 GHz in the electromagnetic spectrum, corresponding to the recommended frequency band of operation of WR12 waveguides. These frequencies are equivalent to wave lengths between 5 mm and 3.333 mm. The E band is in the EHF range of the radio spectrum.
Waveguide is a structure that guides waves, such as electromagnetic waves or sound, with minimal loss of energy by restricting the transmission of energy to one direction. Without the physical constraint of a waveguide, wave amplitudes decrease according to the inverse square law as they expand into three dimensional space.
Broadband is wide bandwidth data transmission which transports multiple signals and traffic types.
Bandwidth is the difference between the upper and lower frequencies in a continuous band of frequencies. It is typically measured in hertz.
Internet Access Rights
 Right to Internet Access states that all people must be able to access
the Internet in order to exercise and enjoy their rights to Freedom of
expression and opinion and other fundamental human rights, that states
have a responsibility to ensure that Internet access is broadly available,
and that states may not unreasonably restrict an individual's access to
the Internet.
Right to Internet Access states that all people must be able to access
the Internet in order to exercise and enjoy their rights to Freedom of
expression and opinion and other fundamental human rights, that states
have a responsibility to ensure that Internet access is broadly available,
and that states may not unreasonably restrict an individual's access to
the Internet.
Media Literacy
Stop Online Piracy Act (wiki)
SOPA Info (youtube)
Net Coalition (twitter)
PIPA - Protect IP Act (wiki)
Support a Free and Open Internet
ITU - International Telecommunication Union - Film
Protect IP Act (youtube)
Controlling the Web (youtube)
Internet Society
Protect Internet Freedom
Center for Democracy & Technology global online civil liberties and human rights, driving policy outcomes that keep the internet open, innovative, and free.
Fight for the Future
F2C2012: Aaron Swartz keynote - "How we stopped SOPA" (youtube)
Pirate Bay (youtube)
Petitioning (start a petition or sign a petition)
How Iran Censors Internet
A2K Network
Why Sopa is a Bad Idea (video)
Firewall is a network security system that monitors and controls the incoming and outgoing network traffic based on predetermined security rules. A firewall typically establishes a barrier between a trusted, secure internal network and another outside network, such as the Internet, that is assumed not to be secure or trusted.
Proxy Server is a server (a computer system or an application) that acts as an intermediary for requests from clients seeking resources from other servers. A client connects to the proxy server, requesting some service, such as a file, connection, web page, or other resource available from a different server and the proxy server evaluates the request as a way to simplify and control its complexity. Proxies were invented to add structure and encapsulation to distributed systems. Today, most proxies are web proxies, facilitating access to content on the World Wide Web and providing anonymity.
Virtual Private Network
DNS Blocking is not the same as Domain Name Filtering used by Internet Browsers for Kids. Censoring Links.
Web Content Control Software or Web Filtering Software is another form of Censorship.
Copyright Information
From July to December 2012, Google Received 2,285 Government Requests to remove 24,179 pieces of content, which is an increase from the 1,811 requests to remove 18,070 pieces of content that we received during the first half of 2012.
United States Computer Emergency Readiness Team
Internet Engineering Task Force
Web Engineering focuses on the methodologies, techniques, and tools that are the foundation of Web application development and which support their design, development, evolution, and evaluation. Web application development has certain characteristics that make it different from traditional software, information system, or computer application development.
Media Literacy - Information Literacy
Internet Infrastructure
Denial-of-Service Attack (wiki)
Internet System Consortium
Bandwidth (signal processing photonics)
Internet Declaration
Kopimism (Missionary Church)
Chaos Communication Congress (wiki)
IT industry consumes between three and five percent of the world’s energy budget. The cost of powering the Internet, which is 1.5% of global electricity, is 8.5 billion dollars annually and is growing at an incredible rate. There are 2.4 billion internet users today, which means more backbone bandwidth, more content, more data centers, more applications, more computers.
Internet Connection Types
 Super Wi-Fi
is using the unused broadcast spectrum. Instead of using the 2.4 GHz radio
frequency of Wi-Fi, the "Super Wi-fi"
proposal uses the lower-frequency white spaces between television channel
frequencies. These lower frequencies allow the signal to travel further
and penetrate walls better than the higher frequencies previously used.
The FCC's plan was to allow those white space frequencies to be used for
free, as happens with shorter-range Wi-Fi and Bluetooth. Rice University,
in partnership with the nonprofit organization Technology For All,
installed the first residential deployment of Super Wi-Fi in east Houston
in April 2011. The network uses white spaces for backhaul and provides
access to clients using 2.4 GHz Wi-Fi. A month later, a public Super Wi-Fi
network was developed in Calgary, Alberta. Calgary based company WestNet
Wireless launched the network for free and paid subscribers. The United
States' first public Super Wi-Fi network was developed in Wilmington,
North Carolina, on January 26, 2012. Florida based company Spectrum
Bridge, Inc. launched the network for public use with access at Hugh
MacRae park. West Virginia University launched the first campus Super WiFi
network on July 9, 2013.
Super Wi-Fi
is using the unused broadcast spectrum. Instead of using the 2.4 GHz radio
frequency of Wi-Fi, the "Super Wi-fi"
proposal uses the lower-frequency white spaces between television channel
frequencies. These lower frequencies allow the signal to travel further
and penetrate walls better than the higher frequencies previously used.
The FCC's plan was to allow those white space frequencies to be used for
free, as happens with shorter-range Wi-Fi and Bluetooth. Rice University,
in partnership with the nonprofit organization Technology For All,
installed the first residential deployment of Super Wi-Fi in east Houston
in April 2011. The network uses white spaces for backhaul and provides
access to clients using 2.4 GHz Wi-Fi. A month later, a public Super Wi-Fi
network was developed in Calgary, Alberta. Calgary based company WestNet
Wireless launched the network for free and paid subscribers. The United
States' first public Super Wi-Fi network was developed in Wilmington,
North Carolina, on January 26, 2012. Florida based company Spectrum
Bridge, Inc. launched the network for public use with access at Hugh
MacRae park. West Virginia University launched the first campus Super WiFi
network on July 9, 2013.WiMAX is a family of wireless broadband communication standards based on the IEEE 802.16 set of standards, which provide multiple physical layer (PHY) and Media Access Control (MAC) options.
LVX System
IPv6 is the most recent version of the Internet Protocol (IP), the communications protocol that provides an identification and location system for computers on networks and routes traffic across the Internet. IPv6 was developed by the Internet Engineering Task Force (IETF) to deal with the long-anticipated problem of IPv4 address exhaustion. IPv6 is intended to replace IPv4. In December 1998, IPv6 became a Draft Standard for the IETF, who subsequently ratified it as an Internet Standard on 14 July 2017.
Radiation (electromagnetic)
White Space (alternate transmission space)
Federal Communications Commission (FCC)
Universal Service Fund (wiki)
A Human Right
Public Knowledge
Internet.org
Internet Modem Battery Backup (brck)
Ushahidi
Open Garden
Broadband Across America
Internet Access is the process that enables individuals and organisations to connect to the Internet using computer terminals, computers, mobile devices, sometimes via computer networks. Once connected to the Internet, users can access Internet services, such as email and the World Wide Web. Internet service providers (ISPs) offer Internet access through various technologies that offer a wide range of data signaling rates (speeds).
Satellite Internet Access is Internet access provided through communications satellites. Modern consumer grade satellite Internet service is typically provided to individual users through geostationary satellites that can offer relatively high data speeds, with newer satellites using Ka band to achieve downstream data speeds up to 50 Mbps.
ViaSat-1
High-Altitude Platform is a station on an object at an altitude of 20 to 50 km and at a specified, nominal, fixed point relative to the Earth.
Google Loon
Universal Service Administrative Company
Fiber-Optic Communication is a method of transmitting information from one place to another by sending pulses of light through an optical fiber. The light forms an electromagnetic carrier wave that is modulated to carry information. Fiber is preferred over electrical cabling when high bandwidth, long distance, or immunity to electromagnetic interference are required.
Optical Fiber Cable - Li-Fi
Passive Optical Network is a telecommunications technology that implements a point-to-multipoint architecture, in which unpowered fiber optic splitters are used to enable a single optical fiber to serve multiple end-points such as customers, without having to provision individual fibers between the hub and customer.
Spectrum Access
NG-PON2 adding new colors of light onto the existing fiber.
In 2015, 2.1 Million People Still Use AOL Dial-Up.
Phone Network - Home Plug
Your Karma WiFi
Hotspot Wi-Fi is a physical location where people may obtain Internet access, typically using Wi-Fi technology, via a wireless local area network (WLAN) using a router connected to an internet service provider.
ZeusPro - Wireless Network Solution Universal non-Electrical Wi-Fi Amplifier. WiFi signal Anywhere.
Fingbox - Network Security & Wi-Fi Troubleshooting.
Beartooth is a handheld device that works with your smartphone to keep you connected when there is no cell service. Your phone connects to your Beartooth using Bluetooth, and your Beartooth connects to other Beartooth devices up to 10 miles away over the 900 MHz ISM band.
Freedom of Speech - First Amendment
Government Websites - About Information Sources
Broadband Subscribership
Information Protection - Is a Website Down or is My Connection a Problem?
Internet Infrastructure
Critical Internet Infrastructure is a collective term for all hardware and software systems that constitute essential components in the operation of the Internet. Physical transmission lines of all types, such as wired, fiber optic and microwave links, along with routing equipment, the accompanying critical software services like the Domain Name System (DNS), Email, website hosting, authentication and authorization, storage systems, and database servers are considered critical Internet components. If any of these systems and services were to be interrupted for a significant period of time "[t]he Internet...as we know it would collapse. Infrastructure.
World Network Map of the Internet Infrastructure Connections and Internet Hubs
Internet Topology Map
Internet Backbone are the principal data routes between large, strategically interconnected computer networks and core routers on the Internet.
Backbone Network is a part of computer network that interconnects various pieces of network, providing a path for the exchange of information between different LANs or subnetworks. A backbone can tie together diverse networks in the same building, in different buildings in a campus environment, or over wide areas. Normally, the backbone's capacity is greater than the networks connected to it.
Network Access Point was a public network exchange facility where Internet service providers (ISPs) connected with one another in peering arrangements.
Core Router is a router designed to operate in the Internet backbone, or core. To fulfill this role, a router must be able to support multiple telecommunications interfaces of the highest speed in use in the core Internet and must be able to forward IP packets at full speed on all of them. It must also support the routing protocols being used in the core. A core router is distinct from an edge router: edge routers sit at the edge of a backbone network and connect to core routers.
Core Network is the central part of a telecommunications network that provides various services to customers who are connected by the access network. One of the main functions is to route telephone calls across the PSTN.
Coding - Networks
Telegeography (telemetry)
How the Internet works: Submarine fibre, brains in jars, and coaxial cables
Internet Connection Speed Testing
Broadband Speed Test
Test My Internet Connection Speed
DSL Reports
Page Loading Speed Test
Webpage Test
Website Speed Test by Country
International Cable Protection Committee
Submarine Communications Cable is a cable laid on the sea bed between land-based stations to carry telecommunication signals across stretches of ocean. The first submarine communications cables, laid in the 1850s, carried telegraphy traffic. Subsequent generations of cables carried telephone traffic, then data communications traffic. Modern cables use optical fiber technology to carry digital data, which includes telephone, Internet and private data traffic. Submarine Cable Map.
Rights to Information - Public Information
 Freedom of Information Act in the United States is a federal
freedom of
information law that allows for the
full or partial disclosure of
previously unreleased information and
documents controlled by the United States government. The Act defines
agency records subject
to disclosure, outlines mandatory disclosure
procedures and grants nine
exemptions
to the statute. Right to Information
mandates a timely response to a citizens request for government
information.
Freedom of Information Act in the United States is a federal
freedom of
information law that allows for the
full or partial disclosure of
previously unreleased information and
documents controlled by the United States government. The Act defines
agency records subject
to disclosure, outlines mandatory disclosure
procedures and grants nine
exemptions
to the statute. Right to Information
mandates a timely response to a citizens request for government
information.Public Records are documents or pieces of information that are not considered confidential and generally pertain to the conduct of government. Information includes Records of law court proceedings. Records of births, marriages, and deaths. Records of land ownership. Statistics regarding population and the economic activity of a country, to name a few. Public records refers to information that has been filed or recorded by public agencies, such as corporate and property records. Public records are created by the federal and local government, (vital records, immigration records, real estate records, driving records, criminal records, etc.) or by the individual.
Right to Know - Need to Know - Public Interest - Open Governance
Transparency - Accountability - Journalism - Watchdogs
Public Information is any information, regardless of form or format, that an agency discloses, disseminates, or makes available to the public.
Public Document can be court records, land deeds, and public registers authenticated by a public officer and made available for public reference and use. Statements by public officers in such documents in their official capacity are admissible evidence of fact in civil matters. Also called public record.
Public Domain consists of all the creative work to which no exclusive intellectual property rights apply. Those rights may have expired, been forfeited, expressly waived, or may be inapplicable.
Center for the Study of the Public Domain - On January 1, 2021, works from 1925 finally enter the U.S. public domain.
Emre Hasan Akbayrak Librarian Blog
Federal Register is the official journal of the federal government of the United States that contains government agency rules, proposed rules, and public notices. It is published every weekday, except on federal holidays. The final rules promulgated by a federal agency and published in the Federal Register are ultimately reorganized by topic or subject matter and codified in the Code of Federal Regulations (CFR), which is updated annually. The Federal Register is compiled by the Office of the Federal Register (within the National Archives and Records Administration) and is printed by the Government Publishing Office. There are no copyright restrictions on the Federal Register; as a work of the U.S. government, it is in the public domain.
Freedom of Information Laws by Country (wiki) - National Freedom of Information Coalition - European Digital Rights
Internal information is any information, oral or recorded in electronic or paper format, maintained by the District or used by the District or its employees.
Access to Knowledge should be linked to fundamental principles of justice, freedom, and economic development.
How to Make an Open Records Request: First review the laws in your state at State Sunshine Laws - How To. Come up with as precise a description as you can of the documents or records you want. Figure out which office -- school district, city government, state agency, etc. -- will have the records or documents you want. Contact that unit of government and ask them who at the agency is responsible for providing copies of documents. Prepare your request using the fully automated, fill-in-the-blanks, state open records letter generator. Mail or email your request, or deliver it in person. Make a note on your calendar of the deadline for the agency to provide you with the documents you've requested. Making any Record Available to a Person under this paragraph, an agency shall provide the record in any form or format requested by the person if the record is readily reproducible by the agency in that form or format. Each agency shall make reasonable efforts to maintain its records in forms or formats that are reproducible for purposes of this section.
California Public Records Act requires inspection or disclosure of governmental records to the public upon request.
Note: Peoples access to information and knowledge is incredibly important. The Freedom of Information Act is under constant attack and our Right to Information is being denied, and even worse, it's also being Manipulated and Censored. With the Internet being filtered and manipulated means that our information is in jeopardy. You have to be diligent and prolific if you want to stay informed and educated about the truth.
Expect professional behavior from the custodians of the records you seek, and behave professionally yourself. If you encounter resistance, document what happened. State Sunshine Laws has information about each state's open records law, including contact information sorted by state for many school districts and city and county governments. Many states have organizations devoted to freedom of information. Don't hesitate to ask for help. If you will want to share information about the documents you receive--what the documents say or reveal--consider starting a blog.
Town Hall Records - All documents are recorded in the clerk's office of the Town or City where the property is located. Land Records itself is a generic expression and can include records such as, the register of lands, Records of Rights (RoRs), tenancy and crop inspection register, mutation register, disputed cases register, etc. Town Clerk's Office serves as a keeper of the records for all documents that pertain to a City. Town Clerk's primary functions is the recording, processing, archiving and retrieval of land records, deeds, mortgages, attachments, tax liens, judgments, maps, floor plans, probate certificates, death notices, variances and all other legal documents pertaining to land use and transfers. The Town Clerk records, and keeps permanent documentation and indices of all transactions.
Criminal Background Checks - Public Records For Arrests, Criminal, Address, Marriage, Property & More! Search Arrest Records. Dark Web Scan. Background Check. Find Anyone's Address. Types: Arrest Records, Traffic Tickets, Addresses, Phone Numbers, Background Checks.
Historical Records - Historical Documents - A record or narrative description of past events. Knowledge Preservation.
Ancestral knowledge - Family Tree
Library of Congress Archives - The Library of Congress Web Archive manages, preserves, and provides access to archived web content selected by subject experts from across the Library, so that it will be available for researchers today and in the future. Websites are ephemeral and often considered at-risk born-digital content. Libraries.
National Archives and Records Administration is the nation's record keeper. Of all documents and materials created in the course of business conducted by the United States Federal government, only 1%-3% are so important for legal or historical reasons that they are kept by us forever. Those valuable records are preserved and are available to you, whether you want to see if they contain clues about your family’s history, need to prove a veteran’s military service, or are researching a historical topic that interests you. (NARA).
U.S. Government Information is a service of the United States Government Publishing Office, which is a Federal agency in the legislative branch. Gov Info provides free public access to official publications from all three branches of the Federal Government.
Homeland Security Digital Library - Securing the homeland through the power of information.
Public Knowledge does not mean that the knowledge is available to everyone. It means that there is knowledge, but only if you know where to find it. And only if you know what questions to ask, and know which people to talk to. Knowledge Gap.
What would you consider to be public information? I have been asking that question for over 12 years, and here's what I found.
Public Relations is the practice of managing the spread of information between an individual or an organization and the public. (PR).
To Be Informed - Knowledge Management - Information Sources
Education is a Human Right, because it's the right thing to do, it's just common sense. Education Reform.
Open Rights Group protects the digital rights of people in the UK including privacy and free speech online. We are powered by more than 20,000 members and supporters like you.
Open Records is a blog about freedom of information, open records and access to public documents. It is associated with WikiFoia, is sponsored by the Lucy Burns Institute and is written by Leslie Graves and Joshua Meyer.
Demand Progress - We work to win progressive policy changes for ordinary people through organizing and grassroots lobbying. We focus on issues of civil liberties, civil rights, and government reform. We run online campaigns to rally people to take action on the news that affects them — by contacting Congress and other leaders, funding pressure tactics, and spreading the word in their own communities. We work in Washington to provide an advocate for the public in all the decisions that affect our lives.
Censorship - Suppression
 Censorship
is the suppression of
free speech and public
communication or
other information without
logical reasons.
Censorship
is the suppression of
free speech and public
communication or
other information without
logical reasons.
Profiling - Discrimination - Free Speech Abuse - Blacklisting - Denial - Secrecy
Censorship is not the same as Filtering or protecting someone from inappropriate material. Whether it's an Adult Mind or a Child's Mind, the lack of knowledge will always create vulnerabilities, risks and dangers. Just because you have a lack of censorship, this does not mean that freedom of speech is protected, because lies and propaganda in the media does a lot of harm and damage to peoples perceptions of reality.
Whistle Blowing - Freedom of Information Act - Right to Information - Everyone is on a Need to Know Basis.
Censorship in the United States is when certain information may be considered objectionable, harmful, sensitive, politically incorrect or inconvenient by governments, media outlets, authorities or other groups or institutions. Censorship is Genocide of the mind if it is used to keep people from knowing the truth. Violence against Journalists.
Internet Censorship is blocking access to websites. Dumbing Down Education (Genocide carried out on paper).
Censure is an expression of strong disapproval or harsh criticism. Rebuke. Banned Books - Challenge Literature.
Media Blackout refers to the censorship of news related to a certain topic, particularly in mass media, for any reason. And when they do talk it is sometimes just propaganda. The Freedom of Information Act is being violated continually.
Block Internet is a technical measure intended to restrict access to information or resources. Blocking and its inverse, unblocking, may be implemented by the owners of computers using software. Some countries, including China and Singapore, block access to certain news information. In the United States, the Children's Internet Protection Act requires schools receiving federal funded discount rates for Internet access to install filter software that blocks obscene content, pornography, and, where applicable, content "harmful to minors". Blocking may also refer to denying access to a web server based on the IP address of the client machine. In certain websites, including social networks such as Facebook or editable databases like Wikimedia projects and other wikis, users can apply blocks (based in either IP number or account) on other users deemed undesirable to prevent them from performing certain actions. Blocks of this kind may occur for several reasons and produce different effects: in social networks, users can unrestrictedly block other users, typically by preventing them from sending messages or viewing the blocker's information or profile. Privileged users can apply blocks that affect the access of the undesirables to the entire website. Blocking is used by moderators and administrators of social media and forums to deny access to users that have broken their rules and will likely do so again, in order to ensure a peaceful and orderly discussion place. Common reasons for blocking are spamming, trolling, and flaming. Some criticize cases of the use of bans by administrators of large websites, such as Twitter, saying that these bans may be politically or financially motivated. However, websites have a legal right to decide who is allowed to post, and users often respond by "voting with their feet" and going to a place where the administrators see their behavior as acceptable.
Blocked Websites by Country (wiki) - Banned Websites Awareness - Comment Section Policing
History being Censored and Propagandized - Book Burning
When people read or hear something that challenges their beliefs, they can ignorantly censor that information without any verification of its accuracy. That is called bias and prejudice. A person needs to be educated in information literacy in order to avoid being biased or prejudice. If not, then they will abuse themselves and abuse other people with devastating consequences, such as death and destruction. Discretion Advised.
Censorship is a form of terrorism. If you stop people from having access to valuable knowledge and information that could save their life, then that is murder.
Humans use language to transmit information and process information, and when language is controlled or manipulated by the media or by educational institutions, then someone can control your mind. And that is a fact that people have confirmed and witnessed. Human language is under attack, which is terrorism of the worst kind, an attack from within.
The Real Danger is not the Internet, the real danger is ignorance. We must learn to balance freedom of expression with the rights of an individual. If people were afraid to speak because they feared being misunderstood, then no one would say anything valuable and everyone would be even more ignorant then they are now. Activism.
The Protection from Online Falsehoods and Manipulation Act is to issue corrections or remove content that the government deems false. Media companies that fail to comply face a fine of up to a 1 million Singapore dollars (about $722,000). Individuals found guilty of violating the law, both inside and outside the tiny Southeast Asian country, could face fines of up to $60,000 or prison for up to 10 years. Opposition lawmakers and free speech advocates in Singapore and around the region say the law will stifle public discussion and hamstring journalists in a country they say is steadily marching further toward authoritarianism.
Bleep Censor has been used for many years as a means of censoring TV programs to remove content not deemed suitable for "family", "daytime", "broadcasting", or "international" viewing and personal information for privacy. The bleep censor is a software module, manually operated by a broadcast technician. A bleep is sometimes accompanied by a digital blur or box over the speaker's mouth in cases where the removed speech may still be easily understood by lip reading. Profanity - Movie Rating System - Time Delay.
Broadcast Delay is an intentional delay when broadcasting live material. Such a delay may be short (often seven seconds) to prevent mistakes or unacceptable content from being broadcast. Longer delays lasting several hours can also be introduced so that the material is aired at a later scheduled time (such as the prime time hours) to maximize viewership. Tape delays lasting several hours can also be edited down to remove filler material or to trim a broadcast to the network's desired run time for a broadcast slot, but this isn't always the case.
Family Viewing Hour had a responsibility to air "family-friendly" programming during the first hour of the prime time lineup (8 to 9 p.m. Eastern Time). The hour disappeared in 1977 after the policy was overturned in court; however, the concept has continued to be used by some viewers who still believe that the 8:00 p.m. time slot in primetime has an obligation to have family-friendly programming.
Self-Censorship is the act of censoring or classifying one's own discourse. This is done out of fear of, or deference to, the sensibilities or preferences (actual or perceived) of others and without overt pressure from any specific party or institution of authority. Self-censorship is often practiced by film producers, film directors, publishers, news anchors, journalists, musicians, and other kinds of authors including individuals who use social media. Self-Censorship is not saying something or writing something because you fear being misunderstood or attacked. Conformity.
You can’t fight diseases, or in this case the dangers of the Internet, by simply isolating, blocking and filtering websites or quarantining children because eventually people will be infected. You fight diseases or dangers by building the immune system just like a vaccine does by giving a small amount of the disease so that the body builds up its immunity to that particular disease. The immune system in this case is a child’s capacity to think logically and to possess extensive knowledge about vulnerabilities and hazards that are on TV, the Internet and at the Library. A teacher or parent needs to explain why certain things are inappropriate, and If a teacher or parent can not teach this then they must learn. Everyone must learn about the importance of moral practices and ethical standards but they must also learn why some things in this world do not have moral practices or ethical standards.
American Censorship - Public Knowledge - Stop Censorship
Media Literacy (human language is under attack)
Copyright Infringement Protection should not violate Constitutional Rights.
Freedom of Speech and The First Amendment (Journalism)
 Redact is to prepare a publication or
presentation by correcting,
revising, adapting or editing text. To censor or obscure part of a
text for legal or security purposes or because someone put text
inappropriate text in a publication. (merging the layers).
Redact is to prepare a publication or
presentation by correcting,
revising, adapting or editing text. To censor or obscure part of a
text for legal or security purposes or because someone put text
inappropriate text in a publication. (merging the layers).Redaction is a form of editing in which multiple source texts are combined (redacted) and altered slightly to make a single document. Often this is a method of collecting a series of writings on a similar theme and creating a definitive and coherent work. The term is also used to describe removal of some document content, replacing it typically with black rectangles which indicate the removal.
Sanitization of classified information is the process of removing sensitive information from a document or other message (or sometimes encrypting it), so that the document may be distributed to a broader audience. When the intent is secrecy protection, such as in dealing with classified information, sanitization attempts to reduce the document's classification level, possibly yielding an unclassified document. When the intent is privacy protection, it is often called data anonymization. Originally, the term sanitization was applied to printed documents; it has since been extended to apply to computer media and the problem of data remanence as well. Redaction in its sanitization sense (as distinguished from its other editing sense) is the blacking out or deletion of text in a document, or the result of such an effort. It is intended to allow the selective disclosure of information in a document while keeping other parts of the document secret. Typically the result is a document that is suitable for publication or for dissemination to others than the intended audience of the original document. For example, when a document is subpoenaed in a court case, information not specifically relevant to the case at hand is often redacted.
Content-Control Software is software designed to restrict or control the content a reader is authorized to access, especially when utilized to restrict material delivered over the Internet via the Web, e-mail, or other means. Content-control software determines what content will be available or be blocked.
Children must learn the difference between being funny and what is insensitive and cruel. Children must also learn that just because something is called entertainment does not mean that it is safe or that it will not have any repercussions or undesirable affects on the human mind. I'm all for Protecting Children from Inappropriate Material as long as someone teaches them why it's not suitable and dangerous. But controlling, limiting or censoring children’s freedoms is not teaching, you are just delaying the fact that they will make mistakes and most likely never learn from their mistakes, with some children being ultimately devastated by their mistakes. The only real protection children have against vulnerabilities and hazards in our world is a very comprehensive and a very effective education. Educate children, communicate with children and learn from children.
Money is a form of Censorship - Human Rights
National Coalition Against Censorship
Lambasted is to censure severely or angrily. Censure is harsh criticism or disapproval.
Exclusion is the act of forcing out someone or something. The state of being excluded. the state of being excommunicated. A deliberate act of omission.
Excluded is to prevent from being included, considered or accepted. Prevent from entering; shut out. Lack or fail to include. Disallow membership or entry. Put out or expel from a place.
Omission is any process whereby sounds or words are left out of spoken words or phrases. Neglecting to do something; leaving out or passing over something. A mistake resulting from neglect.
Omitted is to prevent from being included, considered or accepted. Leave undone or leave out.
Ejected is to put out or expel from a place. Eliminate. Leave an aircraft rapidly, using an ejection seat or capsule. Rejection.
Eliminate is to terminate, end, or take out. Do away with. Dismiss from consideration or a contest. Expel from the body.
Expel is to force to leave or move out. Force to leave or move out. Cause to flee. Expelled. Booted out and remove from a position or office.
Withholding is the act of holding something back or keeping within your possession or control. To hold something back and refuse to hand over or share. To retain and refrain from disbursing payments. Withholding Evidence.
Censorship from Internet Service Providers.
If you see any connection errors on any of the pages on BK101, that means the website might be being blocked and censored. Your right to be knowledgeable and educated might be restricted and denied by criminals.
406 Not Acceptable or Server Not Found The Connection was Reset, the connection to the server was reset while the page was loading. Webpage doesn't load, shows only a blank white screen, while other websites load normally.
Not Acceptable: An appropriate representation of the requested resource could not be found on this server. Error 406 sometimes due to Mod Security updates on the server. (Refresh Browser Window).
Browser Errors are giving warnings saying that the connection is not secure? Most people don't know how to fix these types of errors, so they might believe they can't access the website. Fear Mongering.
Connection Not Secure Warning: Your connection is not private and the information you share on this site can be viewed by others. But why is there a warning on pages that have no inputs? (there may be link on the page that has tracking software, and all they need is authentication from the tracking link to remove the error).
SSL Error is actually just a warning and can be just an information error, so how is a person supposed to know?
HTTP is a system for transmitting information from a web server to your browser. HTTP is not secure, so when you visit a page served over HTTP, your connection is open for eavesdropping and man-in-the-middle attacks. Most websites are served over HTTP because they don't involve passing sensitive information back and forth and do not need to be secured.
When you visit a page fully transmitted over HTTPS, such as your bank, you'll see a green padlock icon in the address bar (For details, see How do I tell if my connection to a website is secure?). This means that your connection is authenticated and encrypted, and thus safeguarded from both eavesdroppers and man-in-the-middle attacks.
However, if the HTTPS page you visit includes HTTP content, the HTTP portion can be read or modified by attackers, even though the main page is served over HTTPS. When an HTTPS page has HTTP content, we call that content “mixed”. The page you are visiting is only partially encrypted and even though it appears to be secure, it isn't.
Content Blocking? Some browsers may protect you from attacks by blocking potentially harmful, insecure content on web pages that are supposed to be secure. (what does that mean?) No Blockable content detected on this page? Some content not secure like images?
The page contains mixed active content? Some browsers do not block insecure elements. That page is open to eavesdropping and attacks where your personal data from the site could be stolen. Unless you’ve unblocked mixed content using the instructions in the next section. Look for Icons.
Not blocking insecure passive content, such as images? By default, Some browsers do not block mixed passive content; you will simply see a warning that the page isn't fully secure. Attackers may be able to manipulate parts of the page like displaying misleading or inappropriate content, but they should not be able to steal your personal data from the site.
Distributed Denial of Service (DDoS) Madory, BackConnect had regularly spoofed internet addresses through a technique known as a “BGP hijack,” an aggressive tactic that pushes the bounds of accepted cyber-security industry practices. "Zombie” machines, referred to as botnets. A botnet is formed of personal computers in homes or offices infected with malicious code which, upon the request of a hacker, can start flooding a web server with data. One or two machines wouldn’t be an issue, but if tens or hundreds of thousands fire such data simultaneously, it can be enough to cripple even the most sophisticated of web servers. Dyn incident, the computers targeted were DNS servers.
Protecting Internet Communications during Protests
Haystack Software program intended for network traffic obfuscation and encryption. It was promoted as a tool to circumvent internet censorship in Iran. Shortly after the release of the first test version, reviewers concluded the software didn't live up to promises made about its functionality and security, and would leave its users' computers more vulnerable.
Fire Chat App - Bitcoin
Mesh Networking is a network topology in which each node relays data for the network. All mesh nodes cooperate in the distribution of data in the network.
Wireless Mesh Network is a communications network made up of radio nodes organized in a mesh topology. It is also a form of wireless ad hoc network. Wireless mesh networks often consist of mesh clients, mesh routers and gateways. The mesh clients are often laptops, cell phones and other wireless devices while the mesh routers forward traffic to and from the gateways which may, but need not, be connected to the Internet. The coverage area of the radio nodes working as a single network is sometimes called a mesh cloud. Access to this mesh cloud is dependent on the radio nodes working in harmony with each other to create a radio network. A mesh network is reliable and offers redundancy. When one node can no longer operate, the rest of the nodes can still communicate with each other, directly or through one or more intermediate nodes. Wireless mesh networks can self form and self heal. Wireless mesh networks can be implemented with various wireless technologies including 802.11, 802.15, 802.16, cellular technologies and need not be restricted to any one technology or protocol. MN.
Glasswire firewall software reveals threats your antivirus missed.
Peer to Peer computing or networking is a distributed application architecture that partitions tasks or workloads between peers. Peers are equally privileged, equipotent participants in the application. They are said to form a peer-to-peer network of nodes.
Peer-to-peer file sharing is the distribution and sharing of digital media using peer-to-peer (P2P) networking technology. P2P file sharing allows users to access media files such as books, music, movies, and games using a P2P software program that searches for other connected computers on a P2P network to locate the desired content. The nodes (peers) of such networks are end-user computers and distribution servers (not required).
Bulletproof Hosting is a service provided by some domain hosting or web hosting firms that allows their customer considerable leniency in the kinds of material they may upload and distribute.
TOR: Private Communications
Anonymous Internet Web Browsing
Identity Obfuscation (PDF)
Mega Proxy
Be-Bound app connects to the Internet even when you have no data connection or WiFi
Private Messaging
Tox
Briar Project
Invisible
Cuban youth build secret computer network despite Wi-Fi ban
Hola is one of the most popular ways to access geo-blocked websites. How to Geek
VPN's or a Virtual Private Network is another option. These allow you to tunnel your traffic through an encrypted connection and come out on the other side.
Shellfire Box VPN Evolution
SIPRNet is "a system of interconnected computer networks used by the U.S. Department of Defense and the U.S. Department of State to transmit classified information (up to and including information classified SECRET) by packet switching over the 'completely secure' environment". It also provides services such as hypertext document access and electronic mail. As such, SIPRNet is the DoD's classified version of the civilian Internet.
Keezel: Protect your privacy and security online! Portable WiFi solution that unblocks content worldwide
Turris Omnia: Hi-Performance Open-Source Router
Code Words
HOLY $H!T - Long Distance Wi-Fi (Up to 25 KILOMETER range!?) (youtube)
Ubiquiti Networks
Linus Tech Tips (youtube channel)
How to Unblock US Websites using DNS Proxy
Protecting The Information Highway
Lantern is a free desktop App that delivers fast, reliable and secure access to the open Internet.
Secure My Email - Smartphones.
Freebrowser is a free App gives access to websites even if they are blocked by national or corporate firewalls.
Data Protection - Safe Web Surfing - Encryption
 Data Protection Act 1998 defines the law on the processing of data on
identifiable living people and is the main piece of legislation that
governs the data protection.
Data Protection Act - Bitcoin.
Data Protection Act 1998 defines the law on the processing of data on
identifiable living people and is the main piece of legislation that
governs the data protection.
Data Protection Act - Bitcoin.Are You Safe?
Information Privacy is the relationship between the collection and dissemination of data, technology, the public expectation of privacy, and the legal and political issues surrounding them. Privacy concerns exist wherever personally identifiable information or other sensitive information is collected, stored, used, and finally destroyed or deleted – in digital form or otherwise. Improper or non-existent disclosure control can be the root cause for privacy issues. Data privacy issues may arise in response to information from a wide range of sources, such as: Healthcare records, Criminal justice investigations and proceedings, Financial institutions and transactions, Biological traits, such as genetic material, Residence and geographic records, Privacy breach, Location-based service and geolocation, Web surfing behavior or user preferences using persistent cookies. The challenge of data privacy is to utilize data while protecting individual's privacy preferences and their personally identifiable information. The fields of computer security, data security, and information security design and utilize software, hardware, and human resources to address this issue. Since the laws and regulations related to Privacy and Data Protection are constantly changing, it is important to keep abreast of any changes in the law and to continually reassess compliance with data privacy and security regulations. Privacy Protection (gov).
Data Protection Directive is the protection of individuals with regard to the processing of personal data and on the free movement of such data.
Privacy Rights - Privacy Policies
None of Your Business or Mind your own Business is a term used to say that something is private and is not your concern, and you should respect other people's privacy. Stop meddling in peoples private affairs. This is a private matter.
Data Breach is the intentional or unintentional release of secure or private/confidential information to an untrusted environment.
Cyberwarfare actions by a nation-state to penetrate another nation's computers or networks for the purposes of causing damage or disruption.
Cyber Security Standards are techniques generally set forth in published materials that attempt to protect the cyber environment of a user or organization.
Information Security is the practice of preventing unauthorized access, use, disclosure, disruption, modification, inspection, recording or destruction of information. The information or data may take any form, e.g. electronic or physical. Information security's primary focus is the balanced protection of the confidentiality, integrity and availability of data (also known as the CIA triad) while maintaining a focus on efficient policy implementation, all without hampering organization productivity. This is largely achieved through a multi-step risk management process that identifies assets, threat sources, vulnerabilities, potential impacts, and possible controls, followed by assessment of the effectiveness of the risk management plan. Physical Security.
Login is the process by which an individual gains access to a computer system by identifying and authenticating themselves. The user credentials are typically some form of "username" and a matching "password".
Access Control is the selective restriction of access to a place or other resource. The act of accessing may mean consuming, entering, or using. Permission to access a resource is called authorization. Locks and login credentials are two analogous mechanisms of access control.
Security Engineering is a specialized field of engineering that focuses on the security aspects in the design of systems that need to be able to deal robustly with possible sources of disruption, ranging from natural disasters to malicious acts. It is similar to other systems engineering activities in that its primary motivation is to support the delivery of engineering solutions that satisfy pre-defined functional and user requirements, but with the added dimension of preventing misuse and malicious behavior. These constraints and restrictions are often asserted as a security policy.
Data Remanence is the residual representation of digital data that remains even after attempts have been made to remove or erase the data. This residue may result from data being left intact by a nominal file deletion operation, by reformatting of storage media that does not remove data previously written to the media, or through physical properties of the storage media that allow previously written data to be recovered. Data remanence may make inadvertent disclosure of sensitive information possible should the storage media be released into an uncontrolled environment (e.g., thrown in the trash or lost).
How Hackers Could Wirelessly Bug Your Office (youtube)
VAULTCARD Protection from RFID Fraud. Pocket-sized protection against RFID fraud, shielding credit cards to keep personal data safe.
Data - Knowledge Management - Freedom to Information
Confidentiality, Integrity, and Availability. Health Records.
Secure Internet Communications
Protecting Internet Communications during Protests
Protecting the Internet - Laws
Replay Attack is a form of network attack in which a valid data transmission is maliciously or fraudulently repeated or delayed. This is carried out either by the originator or by an adversary who intercepts the data and re-transmits it, possibly as part of a masquerade attack by IP packet substitution. This is one of the lower tier versions of a "Man-in-the-middle attack". Another way of describing such an attack is: "an attack on a security protocol using replay of messages from a different context into the intended (or original and expected) context, thereby fooling the honest participant(s) into thinking they have successfully completed the protocol run."
Privacy - Anonymity
 Anonymity
on the Internet,
most commentary on the Internet is
essentially done anonymously, using unidentifiable pseudonyms. While these
usernames can take on an identity of their own, they are frequently
separated and anonymous from the actual author. Anonymizing services such
as I2P and Tor address the issue of IP tracking. In short, they work by
encrypting packets within multiple layers of encryption. The packet
follows a predetermined route through the anonymizing network. Each router
sees the immediate previous router as the origin and the immediate next
router as the destination. Thus, no router ever knows both the true origin
and destination of the packet. This makes these services more secure than
centralized anonymizing services (where a central point of knowledge
exists. Bitcoin.
Anonymity
on the Internet,
most commentary on the Internet is
essentially done anonymously, using unidentifiable pseudonyms. While these
usernames can take on an identity of their own, they are frequently
separated and anonymous from the actual author. Anonymizing services such
as I2P and Tor address the issue of IP tracking. In short, they work by
encrypting packets within multiple layers of encryption. The packet
follows a predetermined route through the anonymizing network. Each router
sees the immediate previous router as the origin and the immediate next
router as the destination. Thus, no router ever knows both the true origin
and destination of the packet. This makes these services more secure than
centralized anonymizing services (where a central point of knowledge
exists. Bitcoin.Right to Privacy is to restrain governmental and private actions that threaten the privacy of individuals. - Privacy.
I2P, the Invisible Internet Project (I2P) is an overlay network and darknet that allows applications to send messages to each other pseudonymously and securely. Uses include anonymous Web surfing, chatting, blogging and file transfers. The software that implements this layer is called an I2P router and a computer running I2P is called an I2P node.
Tor anonymity network is free software for enabling anonymous communication. The name is derived from an acronym for the original software project name "The Onion Router". Tor directs Internet traffic through a free, worldwide, volunteer network consisting of more than seven thousand relays to conceal a user's location and usage from anyone conducting network surveillance or traffic analysis.
Tor Project - Tor Browser - Tor Servers
Whisper Systems Signal App Scalable Encryption Tool.
Crypto Party goal is to pass on knowledge about protecting yourself in the digital space. This can include encrypted communication, preventing being tracked while browsing the web, and general security advice regarding computers and smartphones.
Crypto Christmas - Cutealism
Anonymizer is a tool that attempts to make activity on the Internet untraceable. It is a proxy server computer that acts as an intermediary and privacy shield between a client computer and the rest of the Internet. It accesses the Internet on the user's behalf, protecting personal information by hiding the client computer's identifying information.
Anonysurfer
Pseudonymity meaning 'false name', is a state of disguised identity. The pseudonym identifies a holder, that is, one or more human beings who possess but do not disclose their true names (that is, legal identities). Most pseudonym holders use pseudonyms because they wish to remain anonymous, but anonymity is difficult to achieve, and is often fraught with legal issues. True anonymity requires unlinkability, such that an attacker's examination of the pseudonym holder's message provides no new information about the holder's true name.
Online Tracking Web Privacy Measurement (PDF)
Freedom Hosting - Bit-Coin
Deep Web - Dark Internet - Virus Protection
Encryption Software -Cryptography - Decode - IP Cloaking
Cypherpunk is any activist advocating widespread use of strong cryptography and privacy-enhancing technologies as a route to social and political change.
VPN - Virtual Private Networks (safe browsing)
Anonabox Tor & VPN Router For Privacy, Bypassing Censorship & Deterring Hackers to Fund Draper Bio. Project Blue:
Flter: Privacy & Security Router - VPN protection, malicious ad blocking, and Tor anonymity on all the devices in your home.
Betterspot: A Smart VPN Router or secure online surfing and unblocking websites for All Devices.
InvizBox Go: Privacy & security, wherever you are. Use public Wi-Fi safely. Protect your browsing. Stream blocked shows at home. Block ads. Power bank.
Windscribe desktop application and browser extension to block ads and trackers.
How do you know it's Me?
Authentication is the act of confirming the truth of an attribute of a single piece of data (a datum) claimed true by an entity. In contrast with identification which refers to the act of stating or otherwise indicating a claim purportedly attesting to a person or thing's identity, authentication is the process of actually confirming that identity. It might involve confirming the identity of a person by validating their identity documents, verifying the authenticity of a website with a digital certificate, determining the age of an artifact by carbon dating, or ensuring that a product is what its packaging and labeling claim to be. In other words, authentication often involves verifying the validity of at least one form of identification.
Authentication Methods (wiki) - Identity (who am I?)
Password is a word or string of characters used for user authentication to prove identity or access approval to gain access to a resource (example: an access code is a type of password), which is to be kept secret from those not allowed access.
Biometrics refers to metrics related to human characteristics. Biometrics authentication (or realistic authentication) is used in computer science as a form of identification and access control. It is also used to identify individuals in groups that are under surveillance.
Retinal Scan is a biometric technique that uses the unique patterns on a person's retina blood vessels. It is not to be confused with another ocular-based technology, iris recognition, commonly called an "iris scanner."
Facial Recognition is a computer application capable of identifying or verifying a person from a digital image or a video frame from a video source. One of the ways to do this is by comparing selected facial features from the image and a facial database.
Voice Recognition is the identification of a person from characteristics of voices (voice biometrics). It is also called voice recognition. There is a difference between speaker recognition (recognizing who is speaking) and Speech Recognition (recognizing what is being said).
Identity Management Systems refers to an information system, or to a set of technologies that can be used for enterprise or cross-network identity management. Additional terms are used synonymously with "identity management system" including; Access governance system. Identity and access management system. Entitlement management system. User provisioning system.
Identity Management is the security and business discipline that "enables the right individuals to access the right resources at the right times and for the right reasons". It addresses the need to ensure appropriate access to resources across increasingly heterogeneous technology environments and to meet increasingly rigorous compliance requirements. The terms "identity management" (IdM) and "identity and access management" are used interchangeably in the area of Identity access management. "Identity management" comes under the umbrella of IT security. Identity-management systems, products, applications and platforms manage identifying and ancillary data about entities that include individuals, computer-related hardware, and software applications. IdM covers issues such as how users gain an identity, the protection of that identity and the technologies supporting that protection (e.g., network protocols, digital certificates, passwords, etc.).
Open ID is an open standard and decentralized authentication protocol.
Identity Provider provides identifiers for users looking to interact with a system. Asserts to such a system that such an identifier presented by a user is known to the provider. Possibly provide other information about the user that is known to the provider.
Cookies and Profiling
Researcher ID provides a solution to the author ambiguity problem within the scholarly research community. Each member is assigned a unique identifier to enable researchers to manage their publication lists, track their times cited counts and h-index, identify potential collaborators and avoid author misidentification. In addition, your ResearcherID information integrates with the Web of Science and is ORCID compliant, allowing you to claim and showcase your publications from a single one account. Search the registry to find collaborators, review publication lists and explore how research is used around the world!
Public Key Infrastructure is a set of roles, policies, and procedures needed to create, manage, distribute, use, store, and revoke digital certificates and manage public-key encryption.
Public-Key Cryptography is any cryptographic system that uses pairs of keys: public keys that may be disseminated widely paired with private keys which are known only to the owner. There are two functions that can be achieved: using a public key to authenticate that a message originated with a holder of the paired private key; or encrypting a message with a public key to ensure that only the holder of the paired private key can decrypt it.
Bitcoin - Browsers (virus protection) - Code Words
Public Key Certificate - Digital Certificates - Scalable Provable Data Possession - Dynamic Provable Data Possession.
Lattice-Based Access Control
Privacy and Protecting of Personal Information (data mining)
Privacy Rights - Privacy Policies
Enigma Machine were a series of electro-mechanical rotor cipher machines developed and used in the early- to mid-twentieth century to protect commercial, diplomatic and military communication.
Proton Mai - Electronic Privacy Center - Collusion - Life Lock
Data Retention defines the policies of persistent data and records management for meeting legal and business data archival requirements; although sometimes interchangeable, not to be confused with the Data Protection Act 1998.
Staats Trojaner
The National Security Archive
Public Data Sources - Filtering
Heartbleed Bug is a security bug in the OpenSSL cryptography library, which is a widely used implementation of the Transport Layer Security (TLS) protocol. It was introduced into the software in 2012 and publicly disclosed in April 2014. Heartbleed may be exploited regardless of whether the vulnerable OpenSSL instance is running as a TLS server or client. It results from improper input validation (due to a missing bounds check) in the implementation of the TLS heartbeat extension. Thus, the bug's name derives from heartbeat. The vulnerability is classified as a buffer over-read, a situation where more data can be read than should be allowed.
Crowd Strike
ICANN - Internet Corporation for Assigned Names and Numbers.
Computers - Computer Crimes
Use 256 encryption and a Wpa/wpa2 password - Quantum Key Distribution (wiki)
Dangers of Anonymity and the Psychological Effects of being Anonymous.
Information Security Operations Center is a facility where enterprise information systems are monitored, assessed, and defended, such as web sites, applications, databases, data centers and servers, networks, desktops and other endpoints.
Private Information - Do Not Follow - Do Not Share
Proprietary information Agreement also known as a confidentiality agreement (CA), confidential disclosure agreement (CDA), proprietary information agreement (PIA), or secrecy agreement (SA), is a legal contract between at least two parties that outlines confidential material, knowledge, or information that the parties wish to share with one another for certain purposes, but wish to restrict access to or by third parties. It is a contract through which the parties agree not to disclose information covered by the agreement. An NDA creates a confidential relationship between the parties to protect any type of confidential and proprietary information or trade secrets. As such, an NDA protects non-public business information.
Sensitive Information is the control of access to information or knowledge that might result in loss of an advantage or level of security if disclosed to others. Loss, misuse, modification, or unauthorized access to sensitive information can adversely affect the privacy or welfare of an individual, trade secrets of a business or even the security and international relations of a nation depending on the level of sensitivity and nature of the information.
Family Educational Rights and Privacy Act is a law that governs the access of educational information and records.
Privacy Waiver.
Information Rights Management is a subset of digital rights management (DRM), technologies that protect sensitive information from unauthorized access. It is sometimes referred to as E-DRM or Enterprise Digital Rights Management. This can cause confusion, because digital rights management (DRM) technologies are typically associated with business to consumer systems designed to protect rich media such as music and video. IRM is a technology which allows for information (mostly in the form of documents) to be ‘remote controlled’. This means that information and its control can now be separately created, viewed, edited & distributed. A true IRM system is typically used to protect information in a business-to-business model, such as financial data, intellectual property and executive communications. IRM currently applies mainly to documents and emails.
Classified Information Procedures
Classified Information is material that a government body claims is sensitive information that requires protection of confidentiality, integrity, or availability. Access is restricted by law or regulation to particular groups of people, and mishandling can incur criminal penalties and loss of respect. A formal security clearance is often required to handle classified documents or access classified data.
Data Protection Facts - Privacy Blog - Media Literacy
Information Privacy is the relationship between collection and dissemination of data, technology, the public expectation of privacy, and the legal and political issues surrounding them. Privacy concerns exist wherever personally identifiable information or other sensitive information is collected, stored, used, and finally destroyed or deleted – in digital form or otherwise. Improper or non-existent disclosure control can be the root cause for privacy issues. Data privacy issues can arise in response to information from a wide range of sources, such as: Healthcare records, Criminal justice investigations and proceedings, Financial institutions and transactions, Biological traits, such as genetic material, Residence and geographic records, Ethnicity, Privacy breach, Location-based service and geolocation, Web surfing behavior or user preferences using persistent cookies. The challenge of data privacy is to utilize data while protecting individual's privacy preferences and their personally identifiable information. The fields of computer security, data security and information security design and utilize software, hardware and human resources to address this issue. As the laws and regulations related to Privacy and Data Protection are constantly changing, it is important to keep abreast of any changes in the law and continually reassess compliance with data privacy and security regulations.
List of Personal Information Managers (wiki)
Judicial Watch is an American conservative activist group and self-styled watchdog group that files Freedom of Information Act lawsuits to investigate claimed misconduct by government officials.
Confidentiality - Privacy Rights - Anonymity
Information Rights - Journalism Tools
Copyright Information Websites
The Hacker Wars (Full HD Video 91 min.) - Director: Vivien Lesnik Weisman.
National Security Archive is an investigative journalism center, open government advocate, international affairs research institute, and is the largest repository of declassified U.S. documents outside of the federal government. The National Security Archive has spurred the declassification of more than 10 million pages of government documents by being the leading non-profit user of the U.S. Freedom of Information Act (FOIA), filing a total of more than 50,000 FOIA and declassification requests in its nearly 30-year history. History.
Declassified is the process of documents that used to be classified as secret ceasing to be so restricted, often under the principle of freedom of information. Procedures for declassification vary by country. Papers may be withheld without being classified as secret, and eventually made available.
Privacy Rights - Surveillance Abuses and Dangers
 Espionage is the obtaining of information considered
secret
or confidential without the permission of the holder of the information.
Do you still think that you have nothing to hide?
Espionage is the obtaining of information considered
secret
or confidential without the permission of the holder of the information.
Do you still think that you have nothing to hide?Spying is secretly watching someone to collect information. Not the same as an investigation.
False Flag - Espionage Act of 1917 (wiki)
Treason is the crime of betraying one's country, especially by attempting to kill the sovereign or overthrow the government, or its Constitution.
Traitor is someone who betrays his country by committing treason. Counterintelligence?
Treachery is betrayal of a trust. An act of deliberate betrayal.
Betrayal is aiding an enemy against the interest of one's country. Disloyal. Racket of War.
Sell Out is someone who compromises their integrity, morality, authenticity, or principles in exchange for personal gain, such as money, usually at the expense of other people and at the expense of the environment. Judas betrayed Jesus (wiki).
Stab Someone in the Back is to criminally attack someone when they are not looking and not suspecting that someone is doing harmful things behind their back, something out of view and without their knowledge. Backstabber is a traitor or hypocrite, such as a co-worker or friend assumed trustworthy but who figuratively attacks when one's back is turned.
Two Faced - Ass Kisser - Ponzi - Just following orders - Conformity - Ignorance.
Voyeurism is when a person gets sexual pleasure from watching others who are engaged in intimate behaviors, such as undressing, sexual activity, or other actions that are usually considered to be of a private nature. Hidden Camera.
Private are things deeply personal that should be concealed or hidden from the presence or view of others. Privy is something hidden from general view or use. To be informed about something secret or not generally known.
Privacy - Privacy Policies (disclaimers) - Privileged Information - Discretion - Anonymity
Mind Your Own Business means to respect other people's privacy and stop meddling in other peoples affairs that do not concern you.
Sensitive is being susceptible to the attitudes, feelings, or circumstances of others. Pertaining to classified information.
Infiltration is the action of entering or gaining access to an organization or place surreptitiously, especially in order to acquire secret information or cause damage. Dark Web.
Data Exfiltration occurs when malware and/or a malicious actor carries out an unauthorized data transfer from a computer. It is also commonly called data extrusion or data exportation. Data exfiltration is also considered a form of data theft. Types of data that are targeted includes: Usernames, associated passwords, and other system authentication related information. Information associated with strategic decisions. Cryptographic keys. Personal financial information. Social security numbers and other personally identifiable information (PII). Mailing addresses. United States National Security Agency hacking tools. Three main categories of preventive measures may be the most effective: Preventive, Detective and Investigative.
Data Theft is the act of stealing computer-based information from an unknowing victim with the intent of compromising privacy or obtaining confidential information.
War Crimes - Secrecy - Monopolies - Whistle Blowing
Confidentiality involves a set of rules or a promise that limits access or places restrictions on certain types of information.
Confidential is being entrusted with private and secret information and the having the confidence of another. The level of official classification for documents next above restricted and below secret and available only to persons authorized to see documents so classified.
Classified is information declare unavailable, as for security reasons. Classification of information or documents that are withheld from general circulation. Restriction imposed by the government on documents or technologies that are available only to certain authorized people.
Declassified is having had security classification removed. Lift the restriction on and make available again.
Big Data - Mobile Phone Tracking - Profiling - Cookies - Facial Recognition
Patriot Act is a backronym that stands for Uniting and Strengthening America by Providing Appropriate Tools Required to Intercept and Obstruct Terrorism, such as expand the abilities of law enforcement to expend surveillance, including by tapping domestic and international phones; eased interagency communication to allow federal agencies to more effectively use all available resources in counterterrorism efforts; and increased penalties for terrorism crimes and an expanded list of activities which would qualify someone to be charged with terrorism. Patriot Act is an Act of the United States Congress that was signed into law by U.S. President George W. Bush on October 26, 2001. Roving wiretaps, searches of business records, and conducting surveillance of "lone wolves"—individuals suspected of terrorist-related activities not linked to terrorist groups, now called the USA Freedom Act. - Republican Terrorism.
Diplomatic Cable is a confidential text-based message exchanged between a diplomatic mission, like an embassy or a consulate, and the foreign ministry of its parent country. A diplomatic cable is a type of dispatch. Other dispatches may be sent as physical documents in a diplomatic bag. The term cable derives from the time when the medium for such communications was telegraphs travelling along international submarine communications cables, though over time they have progressed into other formats and pathways. The term cablegram is also sometimes used. Due to the importance and sensitive nature of the subject matter, diplomatic cables are protected by the most elaborate security precautions to prevent unfettered access by the public, and unauthorized interception by foreign governments. Generally digital in format, they are always encrypted, frequently by unbreakable one time pad ciphers using key material distributed using diplomatic couriers.
Non-Disclosure Agreement is a contract through which the parties agree not to disclose information covered by the agreement. It is a legal contract between at least two parties that outlines confidential material, knowledge, or information that the parties wish to share with one another for certain purposes, but wish to restrict access to or by third parties. Doctor–patient confidentiality or physician–patient privilege, attorney–client privilege, priest–penitent privilege, and bank–client confidentiality agreements are examples, often not enshrined in a written contract between the parties. (Non-Disclosure agreement is also known as a confidentiality agreement, confidential disclosure agreement, proprietary information agreement or secrecy agreement).
Your Private Information is being Stolen and Sold. Almost everything that you say or do over a cellphone and the internet can be recorded. And that information can be sold to someone who can then use your information to manipulate you and used to manipulate other people who have also shared similar information that they naively thought was private and secure. These Profiles are being used as a source of violence instead of being used as a source for improvements. "What kind of person would profit from your personal information and then not share that profit with you? Everything that Information exploiters have is from other people. But some how they believe that they earned it, when in fact they just used other people. That's called being a scrounge and a moocher. It's time for the users to give back to the producers. No more free rides. Everyone is responsible for life and the maintenance that we all must do in order to live a beautiful life. No one should be above the law.
Why do some people confide in strangers but not trust a family member or friend with personal information. People will reveal personal information about themselves to strangers, but not reveal anything to their own family. There are some people you can trust and some people you can't trust with personal information, and there are some people we consider to be on a need to know basis. Personal information in the wrong hands is risky. Either you prove that the personal information will never be used in any criminal activity, or you give it back. It's not yours. I am the source of those details, my activities created those details. You went fishing in my pond on my personal property. I added the fish to the pond. Those are my fish. You don't need to steal my fish, you have your own fish and your own pond on your own personal property. So what are you doing? You can tell me. You can trust me and tell me anything, I'm not here to judge you, and I'm not interested in your personal information. Are you safe?
Information Broker is a company which specializes in collecting information about individuals from public records and private sources, including census and change of address records, motor vehicle and driving records, user-contributed material to social networking sites, media and court reports, voter registration lists, consumer purchase histories, most-wanted lists and terrorist watch lists, bank card transaction records, health care authorities, and Web browsing histories. The data are aggregated to create individual profiles, often made up of thousands of pieces of information, such as a person's age, race, gender, height, weight, marital status, religious affiliation, political affiliation, occupation, household income, net worth, home ownership status, investment habits, product preferences and health-related interests. Brokers then sell the profiles to other organizations that use them mainly to target advertising and marketing towards specific groups, to verify a person's identity including for purposes of fraud detection, and to sell to individuals and organizations so they can research people for various reasons. Data brokers also often sell the profiles to government agencies, such as the FBI, thus allowing law enforcement agencies to circumvent laws that protect privacy.
When a corporation says "We were Hacked" or we experienced a Security Breach, this is just another way of saying, "We sold your personal information and blamed it on Hackers", just like when a False Flag Attack blames terrorists. N.S.A. Hacking Tools Stolen? if you want to create a war, you have to give other people weapons. This war tactic is nothing new, it's been used for 100's of years. Shadow Brokers or state sponsored leaks.
Total Information Awareness was a program of the United States Information Awareness Office that began during the 2003 fiscal year. It operated under this title from February until May 2003, before being renamed as the Terrorism Information Awareness.
DARPA LifeLog was a project of the Information Processing Techniques Office of the Defense Advanced Research Projects Agency (DARPA) of the U.S. Department of Defense (DOD).
Information Awareness Office are several DARPA projects focused on applying surveillance and information technology to track and monitor terrorists and other asymmetric threats to U.S. national security by achieving "Total Information Awareness" (TIA). This was achieved by creating enormous computer databases to gather and store the personal information of everyone in the United States without any requirement for a search warrant. Data Collected Included every personal phone call and e-mail, cellphone tracking data, places and countries visited, passports and licenses held, date and place of birth, social network posts, personal photos, likes and dislikes and things you hate, your habits, your biases, books you like, reviews by people who think they know you, dating website profiles, recording of private conversations made in the presence of voice activated technologies or cellphones and pc's, bank accounts, offshore banking accounts, credit cards, late payments, bank records, income records, tax returns, credit history, stocks and bonds, assets, land and property owned, guns and weapons owned, court records, liens & lawsuits, traffic tickets, car accidents, social security number, passwords, user names and aliases, employment history, energy use, medical records, blood type, DNA test results, health information from health tracking devices, race or ethnicity, education back ground, school grades, IQ level, purchases and food buying records, internet searches, every website visited, movies and TV shows watched, background checks on friends and family, family names, friends names, business associates, marriages, sexual orientation, clubs and organizations involved in, voting records, political affiliations, religious background, hair and eye color, height, weight, physical weaknesses, allergies, dental records, and numerous other sources. This information was then analyzed to look for suspicious activities, connections between individuals, and possible threats. Additionally, the program included funding for biometric surveillance technologies that could identify and track individuals using surveillance cameras, and other methods. Following public criticism that the development and deployment of this technology could potentially lead to a mass surveillance system, the IAO was defunded by Congress in 2003. However, several IAO projects continued to be funded and merely run under different names, as revealed by Edward Snowden during the course of the 2013 mass surveillance disclosures. Paranoid delusions has turned into madness and power has corrupted the weak and fragile minds of people who are responsible for protecting Unites States Citizens and also protecting vulnerable people around the world. We have not just lost our way, we have lost our minds. It's time to return to reality. But returning to reality will not happen naturally on its own. We must learn how to return to reality and take the necessary actions to encourage learning. So add that to your data collection.
Industrial Espionage is a form of espionage conducted for commercial purposes instead of purely national security.
Foreign Agents Registration Act requiring that agents representing the interests of foreign powers in a "political or quasi-political capacity" disclose their relationship with the foreign government and information about related activities and finances. The purpose is to facilitate "evaluation by the government and the American people of the statements and activities of such persons."
Foreign Agent is anyone who actively carries out the interests of a foreign country while located in another host country, generally outside the protections offered to those working in their official capacity for a diplomatic mission. Foreign agents may be citizens of the host country.
Counter-intelligence refers to information gathered and activities conducted to protect against espionage, other intelligence activities, sabotage, or assassinations conducted for or on behalf of foreign powers, organizations or persons or international terrorist activities, sometimes including personnel, physical, document or communications security programs.
Any criminal with money can buy surveillance equipment, so your government is not the only corporation that you need to worry about. Scams are worldwide.
EncroChat Secure Communication Tool. THE HAGUE, Netherlands (AP) — European police delivered a major blow to organized crime after cracking an encrypted communications network, allowing them to covertly watch “over the shoulder” of criminals in real time as they planned drug trafficking, arms sales, assassinations and torture, officers announced Thursday. The massive cross-border probe started in 2017 when French police began investigating phones using the EncroChat secure communication tool and ultimately were able to work around the encryption to gain direct access to users’ communications. “It was as though we were sitting at the table where criminals were chatting among themselves really,” said Jannine van den Berg, chief of the Dutch National Police Force. The encrypted platform was used by 60,000 people worldwide, including around 10,000 in Britain, British police said.
Right to Privacy is to restrain governmental and private actions that threaten the privacy of individuals.
Privacy Association is the largest and most comprehensive global information privacy community and resource. Founded in 2000, the IAPP is a not-for-profit organization that helps define, promote and improve the privacy profession globally.
Surveillance Abuses
Surveillance Abuse is the use of surveillance methods or technology to monitor the activity of an individual or group of individuals in a way which violates the social norms or laws of a society. Films about Surveillance Abuses.
Mass Surveillance is the intricate surveillance of an entire or a substantial fraction of a population in order to monitor that group of citizens, often for corrupt purposes. The surveillance is often carried out by local and federal governments or governmental organisations, such as organizations like the NSA and the FBI, but may also be carried out by corporations (either on behalf of governments or at their own initiative). Depending on each nation's laws and judicial systems, the legality of and the permission required to engage in mass surveillance varies. It is often distinguished from targeted surveillance.
Profiling - Facial Recognition - TSA
Keep Tabs On Someone is to watch someone carefully or keep under observation and monitor the activities or any development. To make a conscience effort to know what that person is doing.
How many Cameras does your city have? The total number of cameras in the world could reach 45 billion by 2022, when the global video-surveillance industry is forecast to reach $63 billion. New York City has an estimated 9,000 cameras linked to a system the New York Police Department calls the "Domain Awareness System." But there are more cameras that aren't linked to the system.
Surveillance is the monitoring of behavior, activities, or other changing information for the purpose of influencing, managing, directing, or sometimes protecting people. This can include observation from a distance by means of electronic equipment (such as closed-circuit television (CCTV) cameras) or interception of electronically transmitted information such as Internet traffic or phone calls. It can also include simple no- or relatively low-technology methods such as human intelligence agents and postal interception.
Foreign Intelligence Surveillance Act prescribes procedures for the physical and electronic surveillance and collection of "foreign intelligence information" between "foreign powers" and "agents of foreign powers" (which may include American citizens and permanent residents suspected of espionage or terrorism).
Computer Surveillance is the monitoring of computer activity and data stored on a hard drive, or data being transferred over computer networks such as the Internet.
Targeted Surveillance is a form of surveillance that is targeted on specific persons of interest and distinguished from mass surveillance (or bulk interception). Untargeted surveillance is routinely accused of treating innocent people as suspects in ways that are unfair, of violating human rights, international treaties and conventions as well as national laws and of failing to pursue security effectively. Mobile Phones.
FISA Section 702 is a controversial law that permits U.S. intelligence to Spy on Americans without a warrant when they are detected talking with foreigners overseas who were under surveillance.
How the US Government Spies on People who Protest — including you (video and interactive text)
Operation CHAOS or MH-CHAOS was a Central Intelligence Agency domestic espionage project targeting the American people from 1967 to 1974, established by President Lyndon B. Johnson and expanded under President Richard Nixon, whose mission was to uncover possible foreign influence on domestic race, anti-war and other protest movements. The operation was launched under Director of Central Intelligence (DCI) Richard Helms by chief of counter-intelligence James Jesus Angleton, and headed by Richard Ober. The "MH" designation is to signify the program had a worldwide area of operations.
Interception refers to the facilities in telecommunications and telephone networks that allow law enforcement agencies with court order or other legal authorization to selectively wiretap individual subscribers. Most countries require licensed telecommunications operators to provide their networks with Legal Interception gateways and nodes for the interception of communications. The interfaces of these gateways have been standardized by telecommunication standardization organizations. With the legacy public switched telephone network (PSTN), wireless, and cable systems, lawful interception (LI) was generally performed by accessing the mechanical or digital switches supporting the targets' calls. The introduction of packet switched networks, softswitch technology, and server-based applications the past two decades fundamentally altered how LI is undertaken. Lawful interception differs from the dragnet-type mass surveillance sometimes done by intelligence agencies, where all data passing a fiber-optic splice or other collection point is extracted for storage or filtering. It is also separate from the data retention of metadata that has become a legal requirement in some jurisdictions. Mobile phones are kind of like ankle monitors. they know when you left the house and where you traveled.
Signals Intelligence is intelligence-gathering by interception of signals or communications between people.
Global Surveillance Disclosures
Automatic Number Plate Recognition is a technology that uses optical character recognition on images to read vehicle registration plates. It can use existing closed-circuit television, road-rule enforcement cameras, or cameras specifically designed for the task.
Cellphone Tracking - Wiretaps - Eavesdropping on Conversations
Telephone Tapping is the monitoring of telephone and Internet conversations by a third party, often by covert means.
Eavesdropping is secretly listening to the private conversation of others without their consent. Eavesdropping is the act of secretly or stealthily listening to the private conversation or communications of others without their consent. The practice is widely regarded as unethical, and in many jurisdictions is illegal.
Covert Listening Device is more commonly known as a bug or a wire, is usually a combination of a miniature radio transmitter with a microphone. The use of bugs, called bugging, or wiretapping is a common technique in surveillance, espionage and police investigations.
IMSI-Catcher is a telephone eavesdropping device used for intercepting mobile phone traffic and tracking movement of mobile phone users. Essentially a fake mobile tower acting between the target mobile phone and the service provider's real towers, it is considered a man-in-the-middle (MITM) attack. IMSI-catchers are used in some countries by law enforcement and intelligence agencies, but their use has raised significant civil liberty and privacy concerns and is strictly regulated in some countries such as under the German Strafprozessordnung (German) (StPO / Code of Criminal Procedure). Some countries do not even have encrypted phone data traffic (or very weak encryption), thus rendering an IMSI-catcher unnecessary.
WatchHound Cell Phone Monitor - Patriot Act
Electronic Tagging is a form of surveillance which uses an electronic device, fitted to the person. In some jurisdictions, an electronic tag fitted above the ankle is used for people as part of their bail or probation conditions. It is also used in healthcare settings and in immigration contexts in some jurisdictions. Electronic tagging can be used in combination with the global positioning system (GPS). For short-range monitoring of a person that wears an electronic tag, radio frequency technology is used.
House Arrest - Internment - Slave Labor
Mobile Phone Tracking is the ascertaining of the position or location of a mobile phone, whether stationary or moving. Localization may occur either via multilateration of radio signals between (several) cell towers of the network and the phone, or simply via GPS. To locate a mobile phone using multilateration of radio signals, it must emit at least the roaming signal to contact the next nearby antenna tower, but the process does not require an active call. The Global System for Mobile Communications (GSM) is based on the phone's signal strength to nearby antenna masts.
Stingray Phone Tracker is an IMSI-catcher, a controversial cellular phone surveillance device, manufactured by Harris Corporation. Initially developed for the military and intelligence community, the StingRay and similar Harris devices are in widespread use by local and state law enforcement agencies across the United States and possibly covertly in the United Kingdom.
17 Fake Cell Towers - Hailstorm.
Triggerfish Surveillance describes a technology of cell phone interception and surveillance using a mobile cellular base station (microcell or picocell). The devices are also known as cell-site simulators or digital analyzers.
Pegasus is spyware that can be installed on devices running some versions of iOS, Apple's mobile operating system, as well on devices running Android. It was developed by the Israeli cyberarms firm NSO Group. Discovered in August 2016 after a failed attempt at installing it on an iPhone belonging to a human rights activist, an investigation revealed details about the spyware, its abilities, and the security vulnerabilities it exploited. Pegasus is capable of reading text messages, tracking calls, collecting passwords, mobile phone tracking, accessing and activating microphone and video camera, as well as, gathering information from apps.
NSO Group is an Israeli technology firm whose spyware called Pegasus enables the remote surveillance of smartphones. It was founded in 2010.
WhatsApp snooping scandal on October 30, 2019, WhatsApp's parent company Facebook confirmed that Pegasus, a sophisticated snooping software developed by Israel's NSO Group, was used to target Indian journalists, activists, lawyers and senior government officials. The journalists and activists are believed to have been targets of surveillance for a two-week period until May, when the Indian national election was held.
NSA collected more than 151 million records of Americans' phone calls in 2016, even after Congress limited its ability to collect bulk phone records.
Zero-Click mobile phone attacks require no e-mail link to click on, it simply calls your number to take control of your phone. Zero-click attacks often target apps that provide messaging or voice calling because these services are designed to receive and parse data from untrusted sources. Attackers generally use specially formed data, such as a hidden text message or image file, to inject code that compromises the device. Zero-click attacks, also known as interactionless or fully remote attacks, bypass the need for social engineering entirely, giving threat actors the ability to take over a smartphone in real time without any interaction with the target.
Thin Thread program involved wiretapping and sophisticated analysis of the resulting data.
Warrant a specific type of authorization which permits an otherwise illegal act that would violate individual rights and affords the person executing the writ protection from damages if the act is performed. FISA Warrant - Search Warrant.
United States Foreign Intelligence Surveillance Court is a U.S. federal court established and authorized under the Foreign Intelligence Surveillance Act of 1978 (FISA) to oversee requests for surveillance warrants against foreign spies inside the United States by federal law enforcement and intelligence agencies. Such requests are made most often by the National Security Agency (NSA) and the Federal Bureau of Investigation (FBI). Congress created FISA and its court as a result of the recommendations by the U.S. Senate's Church Committee. Its powers have evolved to the point that it has been called "almost a parallel Supreme Court.
Infiltrate is to enter a group or organization in order to spy on the members.
Indefinite Detention without Trial is the incarceration of an arrested person by a national government or law enforcement agency without a trial, and violates many national and international laws, including human rights laws. Indefinite detention of United States citizens on U.S. soil and abroad without due process. This allows the government to hold anyone deemed to be a threat to be held without a trial, which is a clear violation of the US Constitution that denies the basic rights of a free people. Restore the 4th.
Gamma International
Trading with the Enemy Act says don't help or support scumbags who violate Human Rights, including people and leaders in your own country. Immunity?
Trading with the Enemy Act of 1917 restrict trade with countries hostile to the United States, that includes American Corporations.
Official Secrets Act is legislation that provides for the protection of state secrets and official information, mainly related to national security.
Foreign Intelligence Surveillance Act prescribes procedures for the physical and electronic surveillance and collection of "foreign intelligence information" between "foreign powers" and "agents of foreign powers" (which may include American citizens and permanent residents suspected of espionage or terrorism). It has been repeatedly amended since the September 11. attacks. Hacking Team.
Means, Motive, and Opportunity
Eye in the Sky - The Alan Parsons Project - I am the eye in the sky, Looking at you I can read your mind, I am the maker of rules, Dealing with fools, I can cheat you blind.
Tempora is the codeword for a formerly secret computer system that is used by the British Government Communications Headquarters (GCHQ).
Privacy Law refers to the laws that deal with the regulation of personal information about individuals, which can be collected by governments and other public as well as private organizations and its storage and use. Privacy laws are considered in the context of an individual's privacy rights or reasonable expectation of privacy.
Data Mining (Information Overload)
Under International Maritime Law, every passenger boat must be equipped with an automatic identification system that is to remain on at all times. This allows for tracking boats in real time and helps prevent collisions in fog and bad weather. Anyone with a computer and an Internet connection can click to see what kind of vessels are sailing, where they've recently been and which country they are from. people have figured out that they are being tracked through their transponders, which is a device that, upon receiving a signal, emits a different signal in response.
Citizen Lab studies information controls—such as network surveillance and content filtering—that impact the openness and security of the Internet and that pose threats to human rights. The Citizen Lab collaborates with research centres, organizations, and individuals around the world, and uses a "mixed methods" approach, which combines computer-generated interrogation, data mining, and analysis with intensive field research, qualitative social science, and legal and policy analysis methods.
Electronic Frontier Foundation provides funds for legal defense in court, presents amicus curiae briefs, defends individuals and new technologies from what it considers abusive legal threats, works to expose government malfeasance, provides guidance to the government and courts, organizes political action and mass mailings, supports some new technologies which it believes preserve personal freedoms and online civil liberties, maintains a database and web sites of related news and information, monitors and challenges potential legislation that it believes would infringe on personal liberties and fair use and solicits a list of what it considers abusive patents with intentions to defeat those that it considers without merit.
Amnesty International has more than seven million members and supporters around the world with a stated mission to campaign for a world in which every person enjoys all of the human rights enshrined in the Universal Declaration of Human Rights and other international human rights instruments. Amnesty International is a non-governmental organization founded in London in 1961.
Tracking Your Internet Browsing Activity
Cookie is a small piece of data sent from a website and stored on the user's computer by the user's web browser while the user is browsing. Cookies were designed to be a reliable mechanism for websites to remember stateful information (such as items added in the shopping cart in an online store) or to record the user's browsing activity (including clicking particular buttons, logging in, or recording which pages were visited in the past). They can also be used to remember arbitrary pieces of information that the user previously entered into form fields such as names, addresses, passwords, and credit card numbers. The tracking cookies, and especially third-party tracking cookies, are commonly used as ways to compile long-term records of individuals' browsing histories – a potential privacy concern that prompted European and U.S. lawmakers to take action in 2011.
Super Cookie is a type of browser cookie that is designed to be permanently stored on a user’s computer. Super cookies are generally more difficult for users to detect and remove from their devices because they cannot be deleted in the same fashion as regular cookies. Super cookies serve the same function as regular cookies in that they can contain just about any information including browsing history, authentication details or ad-targeting data. Cookie Central.
3rd Party Cookies, you only need them on certain websites when you are accessing certain information that requires 3rd party cookies to be excepted in order for certain software functions to work properly, like forms or windows that need to open.
Virus Protection - Profiling Dangers - TSA
Biometrics refers to metrics related to human characteristics. Biometrics authentication (or realistic authentication) is used in computer science as a form of identification and access control. It is also used to identify individuals in groups that are under surveillance. Biometrics are body measurements and calculations related to human characteristics. Biometrics authentication (or realistic authentication) is used in computer science as a form of identification and access control. It is also used to identify individuals in groups that are under surveillance. Biometric identifiers are the distinctive, measurable characteristics used to label and describe individuals. Biometric identifiers are often categorized as physiological versus behavioral characteristics. Physiological characteristics are related to the shape of the body. Examples include, but are not limited to fingerprint, palm veins, face recognition, DNA, palm print, hand geometry, iris recognition, retina and odour/scent. Behavioral characteristics are related to the pattern of behavior of a person, including but not limited to typing rhythm, gait, keystroke, signature, behavioral profiling, and voice. Some researchers have coined the term behaviometrics to describe the latter class of biometrics. More traditional means of access control include token-based identification systems, such as a driver's license or passport, and knowledge-based identification systems, such as a password or personal identification number. Since biometric identifiers are unique to individuals, they are more reliable in verifying identity than token and knowledge-based methods; however, the collection of biometric identifiers raises privacy concerns about the ultimate use of this information. It is possible that data obtained during biometric enrollment may be used in ways for which the enrolled individual has not consented. One advantage of passwords over biometrics is that they can be re-issued. Private biometrics is a form of encrypted biometrics. False match rate is the probability that the system incorrectly matches the input pattern to a non-matching template in the database. False non-match rate is the probability that the system fails to detect a match between the input pattern and a matching template in the database.
Biopower relates to the practice of modern nation states and their regulation of their subjects through "an explosion of numerous and diverse techniques for achieving the subjugations of bodies and the control of populations.
Biopolitics the strategies and mechanisms through which human life processes are managed under regimes of authority over knowledge, power, and the processes of subjectivation.
User Profile is a visual display of personal data associated with a specific user, or a customized desktop environment. A profile refers therefore to the explicit digital representation of a person's identity. A user profile can also be considered as the computer representation of a user model.
Biodata is biographical data, factual kinds of questions about life and work experiences, as well as items involving opinions, values, beliefs, and attitudes that reflect a historical perspective.
Digital Footprint refers to one's unique set of traceable digital activities, actions, contributions and communications manifested on the Internet or on digital devices. Digital footprints can be classified as either passive or active. The former is composed of a user's web-browsing activity and information stored as cookies, while the latter is often released deliberately by a user with the intent of sharing information on websites or social media. While the term usually applies to an individual person, digital footprint can also refer to a business, organization or corporation. The use of a digital footprint has both positive and negative consequences. On one hand, it is the subject of many privacy issues. For example, without an individual’s authorization, strangers are able to piece together information about that individual by simply using search engines, and corporations are also able to produce customized ads based on browsing history. On the other hand, others can reap the benefits by profiting off their digital footprint as social media influencers. Furthermore, employers use a candidate’s digital footprint for online vetting and assessing fit due to its reduced cost and accessibility—between two equal candidates, a candidate with a positive digital footprint may have an advantage. As technology usage becomes more widespread, even children are generating larger digital footprints with potential positive and negative consequences such as college admissions. Since it is hard to not have a digital footprint, it is in one’s best interest to create a positive one. Passive digital footprints can be stored in many ways depending on the situation. In an online environment, a footprint may be stored in an online data base as a "hit". This footprint may track the user IP address, when it was created, and where they came from; with the footprint later being analyzed. In an offline environment, a footprint may be stored in files, which can be accessed by administrators to view the actions performed on the machine, without seeing who performed them. Active digital footprints can also be stored in many ways depending on the situation. In an online environment, a footprint can be stored by a user being logged into a site when making a post or change, with the registered name being connected to the edit. In an offline environment a footprint may be stored in files, when the owner of the computer uses a keylogger, so logs can show the actions performed on the machine, and who performed them. One feature of keylogger monitors the clipboard for any changes. This may be problematic as the user may copy passwords or take screenshots of sensitive information which is then logged. Digital footprints are not a digital identity or passport, but the content and meta data collected impacts internet privacy, trust, security, digital reputation, and recommendation. Digital Footprint is created when data is collected without the owner knowing, where as active digital footprints are created when personal data is released deliberately by a user for the purpose of sharing information about oneself by means of websites or social media.
Lifelog is the phenomenon whereby people record their own daily life in varying amount of detail, for a variety of purposes. The record contains a more or less comprehensive dataset of a human's life and activities. The data could be mined to increase knowledge about how people live their lives. In recent years the data is usually captured automatically by wearable technology or mobile devices. People who keep lifelogs about themselves are known as lifeloggers (or sometimes lifebloggers or lifegloggers).
Metadata is "data that provides information about other data, relating to emails, telephone calls, web pages, video traffic, IP connections and cell phone locations. Descriptive metadata describes a resource for purposes such as discovery and identification. It can include elements such as title, abstract, author, and keywords. Structural metadata indicates how compound objects are put together, for example, how pages are ordered to form chapters. Administrative metadata provides information to help manage a resource, such as when and how it was created, file type and other technical information, and who can access it.
Tag Metadata - Keywords - Profiling - Patriot Act
General Data Protection Regulation is a regulation in EU law on data protection and privacy for all individuals within the European Union and the European Economic Area. It also addresses the export of personal data outside the EU and EEA. The GDPR aims primarily to give control to citizens and residents over their personal data and to simplify the regulatory environment for international business by unifying the regulation within the EU.
What is GDPR? - BBC Click (youtube)
Datacoup is a personal data marketplace connect data from the apps and services you already use.
Information Broker collects information about individuals from public records and private sources including census and change of address records, motor vehicle and driving records, user-contributed material to social networking sites such as Facebook, Twitter and LinkedIn, media and court reports, voter registration lists, consumer purchase histories, most-wanted lists and terrorist watch lists, bank card transaction records, health care authorities, and web browsing histories. The data are aggregated to create individual profiles, often made up of thousands of individual pieces of information such as a person's age, race, gender, height, weight, marital status, religious affiliation, political affiliation, occupation, household income, net worth, home ownership status, investment habits, product preferences and health-related interests. Brokers then sell the profiles to other organizations that use them mainly to target advertising and marketing towards specific groups, to verify a person's identity including for purposes of fraud detection, and to sell to individuals and organizations so they can research people for various reasons. Data brokers also often sell the profiles to government agencies, such as the FBI, thus allowing law enforcement agencies to circumvent laws that protect privacy.
Intelligence Analysis is the application of individual and collective cognitive methods to weigh data and test hypotheses within a secret socio-cultural context. The descriptions are drawn from what may only be available in the form of deliberately deceptive information; the analyst must correlate the similarities among deceptions and extract a common truth. Although its practice is found in its purest form inside national intelligence agencies, its methods are also applicable in fields such as business intelligence or competitive intelligence.
Electronic Communications Privacy Act is to extend government restrictions on wire taps from telephone calls to include transmissions of electronic data by computer.
Senate votes to let ISPs sell your Web browsing history to advertisers. The US Senate today voted to eliminate broadband privacy rules that would have required ISPs to get consumers' explicit consent before selling or sharing Web browsing data and other private information with advertisers and other companies.
Online Tracking - Web Privacy Measurement (PDF)
Behavioral Targeting comprises a range of technologies and techniques used by online website publishers and advertisers aimed at increasing the effectiveness of advertising using user web-browsing behavior information. In particular, "behavioral targeting uses information collected from an individual's web-browsing behavior (e.g., the pages that they have visited or searched) to select advertisements to display".
Tailored Access Operations is a cyber-warfare intelligence-gathering unit of the National Security Agency (NSA).
Suspicious Activity Database - NSA Warrantless Surveillance Controversy (wiki)
Cellebrite is an Israeli company that manufactures data extraction, transfer and analysis devices for cellular phones and mobile devices.
PRISM surveillance program under which the NSA collects internet communications from at least nine major US internet companies.
ECHELON is a surveillance program (signals intelligence / SIGINT collection and analysis network) operated on behalf of the five signatory nations to the UKUSA Security Agreement—Australia, Canada, New Zealand, the United Kingdom and the United States, also known as the Five Eyes.
Stellar Wind is the code name of information collected under the President's Surveillance Program (PSP)
The Nationwide SAR Initiative - Tripwire
Google Is a Dragnet for the Police. Google geofence warrants done in secret, sometimes leading to false accusations. Google location services and sweeping searches of phone data of 100's of people to find one person.
Level 3 Communications operated a Tier 1 network, which is an Internet Protocol (IP) network that can reach every other network on the Internet solely via settlement-free interconnection (also known as settlement-free peering). Tier 1 networks can exchange traffic with other Tier 1 networks without having to pay any fees for the exchange of traffic in either direction, while some Tier 2 networks and all Tier 3 networks must pay to transmit traffic on other networks.
Police officers across the country misuse confidential law enforcement databases to get information on romantic partners, business associates, neighbors, journalists and others for reasons that have nothing to do with daily police work, an Associated Press investigation has found.
Trailblazer Project is a program intended to develop a capability to analyze data carried on communications networks like the Internet. It was intended to track entities using communication methods such as cell phones and e-mail.
More Corporate Crimes - Health Records
Smith Act set criminal penalties for advocating the overthrow of the U.S. government and required all non-citizen adult residents to register with the government.
Pentagon to boost cyber security force
Computer Security is the protection of computer systems from the theft or damage to the hardware, software or the information on them, as well as from disruption or misdirection of the services they provide.
Burglars Use Bluetooth Scanners to Find Laptops and Phones. Bluetooth Smart Scanner is the fastest app to find all Bluetooth Smart devices around you. It shows detailed information that Bluetooth Smart devices advertise, including device name, signal strength (RSSI), supported services, battery level, etc.
"The Insider threat is our own Government, and the corporations who own our politicians. Together they're subverting the Constitution."
First comes Mass Surveillance then the Police State.
FBI Criminal, Cyber, Response, and Services Branch was created in 2002 as part of the U.S. government's post-911 response, the CCRSB is responsible for investigating financial crime, white-collar crime, violent crime, organized crime, public corruption, violations of individual civil rights, and drug-related crime. In addition, the Branch also oversees all computer-based crime related to counterterrorism, counterintelligence, and criminal threats against the United States.
Let us avoid another Shit Storm. This mass collection of information is the same thing that the Nazi's did. Our Government claims it's for Security reasons, which we know is a white lie. You're not using this information on peoples behalf, or to benefit people, or to protect people, you're using this information to profit from it, just like any scumbag corporation would. And you're also selling this information to other scumbag criminals at a hefty price. And on top of that you're also using this information to manipulate people, to control people, to blackmail people, and to incriminate people. You have raped humankind for the last time. It's time for your rehabilitation, your education, your realization. You are now going to feel like a child who just realized that the world is not what they thought it was. And that you're not in power, you're just living in a delusional dream, which is a reality and a nightmare for everyone else. But the good news is that you can wake up. Brain Plasticity + Learning = Change. So all is not lost, we can turn this clusterf*ck around and use this information, and our information collection abilities, for good instead of using it for evil purposes. We have a lot to learn, but luckily humans have brains with enormous memory capacity. Sounds familiar?
I Know There's Something Going On - Frida (youtube)
"What are you planning to calculate with those details?"
National Security Letter is an administrative subpoena issued by the United States federal government to gather information for national security purposes. NSLs do not require prior approval from a judge. The Stored Communications Act, Fair Credit Reporting Act, and Right to Financial Privacy Act authorize the United States federal government to seek such information that is "relevant" to authorized national security investigations. By law, NSLs can request only non-content information, for example, transactional records and phone numbers dialed, but never the content of telephone calls or e-mails. NSLs typically contain a nondisclosure requirement, frequently called a "gag order", preventing the recipient of an NSL from disclosing that the FBI had requested the information. The nondisclosure order must be authorized by the Director of the FBI, and only after he or she certifies "that otherwise there may result a danger to the national security of the United States, interference with a criminal, counterterrorism, or counterintelligence investigation, interference with diplomatic relations, or danger to the life or physical safety of any person." Even then, the recipient of the NSL may still challenge the nondisclosure order in federal court. The constitutionality of such nondisclosure orders has been repeatedly challenged. The requirement was initially ruled to be unconstitutional as an infringement of free speech in the Doe v. Gonzales case, but that decision was later vacated in 2008 by the Second Circuit Court of Appeals after it held the USA PATRIOT Improvement and Reauthorization Act gave the recipient of an NSL that included a nondisclosure order the right to challenge the nondisclosure order in federal court. In March 2013, district court judge Susan Illston of Federal District Court in San Francisco struck down the law, writing that the prohibition on disclosure of receipt of an NSL made the entire statute impermissibly overbroad under the First Amendment. On August 24, 2015, the Ninth Circuit Court of Appeals vacated the district court's decision and remanded the case back to the district court for further proceedings.
Administrative Subpoena a subpoena issued by a federal agency without prior judicial oversight. Critics say that administrative subpoena authority is a violation of the Fourth Amendment to the United States Constitution.
Stored Communications Act is a law that addresses voluntary and compelled disclosure of "stored wire and electronic communications and transactional records" held by third-party internet service providers (ISPs). It was enacted as Title II of the Electronic Communications Privacy Act of 1986 (ECPA).
Fair Credit Reporting Act is U.S. Federal Government legislation enacted to promote the accuracy, fairness, and privacy of consumer information contained in the files of consumer reporting agencies.
Right to Financial Privacy Act gives the customers of financial institutions the right to some level of privacy from government searches.
Information Awareness Office in January 2002 to bring together several DARPA projects focused on applying surveillance and information technology to track and monitor terrorists and other asymmetric threats to U.S. national security by achieving "Total Information Awareness" (TIA).
FinFisher also known as FinSpy, is surveillance software marketed by Lench IT solutions PLC with a UK-based branch Gamma International Ltd in Andover, England, and a Germany-based branch Gamma International GmbH in Munich, which markets the spyware through law enforcement channels.
NSA Theme Song - Every Breath You Take, By the Police (youtube)
Glenn Greenwald: Why Privacy Matters (video)
The Third-Party Doctrine is a United States legal theory that holds that people who voluntarily give information to third parties—such as banks, phone companies, internet service providers (ISPs), and e-mail servers—have "no reasonable expectation of privacy. A lack of privacy protection allows the United States government to obtain information from third parties without a legal warrant and without otherwise complying with the Fourth Amendment prohibition against search and seizure without probable cause and a judicial search warrant. Libertarians typically call this government activity unjustified spying and a violation of individual and privacy rights.
Films about Surveillance Abuse
Naked Citizens - World (youtube)
Edward Snowden: Here is how we take back the Internet (video)
State of Surveillance' with Edward Snowden and Shane Smith (FULL EPISODE) (youtube)
Heather Brooke: My Battle to Expose Government Corruption (youtube)
Hubertus Knabe: The Dark Secrets of a Surveillance State (video)
Your Cell Phone Company is Watching (video)
Mikko Hypponen: Three Types of Online Attack (video)
Avi Rubin: All your Devices can be Hacked (video)
VICE Meets Glenn Greenwald: Snowden's Journalist of Choice (youtube)
Big Brother Big Business: Another film about Data Mining and the information War (video)
Activist Repression, FBI Activities, & the AR Movement - Ryan Shapiro (youtube)
A Video about how your personal information is being sold - Dispatches - The Data Theft Scandal (video)
Filming Police.
Surveillance Cameras don't reduce Crime, they just cause more crime to happen in other places, like in our Government.
America’s Surveillance State 1 (The Surveillance Machine) (youtube)
TalkingStickTV - Robert Scheer - They Know Everything About You (youtube 1:08:40) Robert Scheer
An Eye on You: Citizens Under Surveillance Citizens of the 21st century are the focus of prying eyes, whether they agree to it or not. This investigation identifies the stakes and scandals of global surveillance and opens up the debate on our threatened individual freedoms. Aired: 03/27/2016 | 54 min..
Citizens Under Surveillance (youtube)
The Haystack Documentary Investigation into 21st century surveillance in the UK and the Investigatory Powers (IP) Bill currently before Parliament.
How China is creating the world’s largest prison | Four Corners (youtube).
Citizens' Commission to Investigate the FBI: 1971 (youtube) - On March 8, 1971, a group of citizens (aka The Citizens' Commission to Investigate the FBI) broke into a small FBI office in Media Pennsylvania, took every file, and shared them with the public and news outlets. Their actions exposed the FBI's illegal Surveillance Program of law-abiding Americans. Now, these previously anonymous Americans publicly share their story for the first time. The Camden 28 (wiki).
COINTELPRO was a series of covert, and at times illegal, projects conducted by the United States Federal Bureau of Investigation (FBI) aimed at surveilling, infiltrating, discrediting, and disrupting domestic political organizations.
Mass Surveillance - Observation Flaws - Espionage - Power Corruption
Panopticon concept of the design is to allow all (pan-) inmates of an institution to be observed (-opticon) by a single watchman without the inmates being able to tell whether or not they are being watched. Although it is physically impossible for the single watchman to observe all cells at once, the fact that the inmates cannot know when they are being watched means that all inmates must act as though they are watched at all times, effectively controlling their own behaviour constantly. The name is also a reference to Panoptes from Greek mythology; he was a giant with a hundred eyes and thus was known to be a very effective watchman.
Drones (automatous)
Time to turn those cameras around and start filming the real criminals. Since officers started wearing body cameras complaints against officers fell 88%, and the use of force dropped 60%. So if cameras worked in controlling that criminal behavior of police, then they will also help control criminal behavior of bankers, presidents, politicians and corporations. And since we already have enough cameras, it's just a matter of direction and focus.
Nanny State are policies that are overprotective and interfering unduly with personal choice. The term "nanny state" likens government to the role that a nanny has in child rearing.
Mosaic Theory is a method used by American intelligence analysts.
Social Engineering refers to psychological manipulation of people into performing actions or divulging confidential information. A type of confidence trick for the purpose of information gathering, fraud, or system access, it differs from a traditional "con" in that it is often one of many steps in a more complex fraud scheme.
Home Monitoring (security)
The only effective counterterrorism is improving education and public knowledge
Google was Asked to Remove 345 Million Pirate Links in 2014 (who's verifying all these requests?)
Cyber Intelligence Sharing and Protection Act (CISPA) is a proposed law in the United States which would allow for the sharing of Internet traffic information between the U.S. government and technology and manufacturing companies.
United States Foreign Intelligence Surveillance Court is to oversee requests for surveillance warrants against foreign spies inside the United States by federal law enforcement and intelligence agencies.
Computer Fraud and Abuse Act limiting federal jurisdiction to cases "with a compelling federal interest-i.e., where computers of the federal government or certain financial institutions are involved or where the crime itself is interstate in nature."
Songs about secretly watching someone.
Every Breath You Take, I'll be watching you - The Police (youtube)
Somebody's Watching Me - Rockwell (youtube)
Cyber Threats or Cyber Hackers actually make our computer systems safer and more stable because hackers make us more aware of our vulnerabilities and software flaws. This way we can secure them properly, and make sure our systems have backups, as well as, Fail Safe methods that include protections against total power failure. Where human manual labor is the final step in guaranteeing that systems operate normally. So this is not just a software issue, this is a human issue. People need to be educated about system failures and vulnerabilities, and the options and choices that we have during these failures. We don't need another 911 where Cyber Warfare is used as an excuse for the government and the military to attack citizens and the internet. "They cause the problem, and then they try to sell us a cure, which is not a cure, just part of the same problem." So a Cyber War is not our biggest threat, corruption is our biggest threat, and corruption has been our biggest threat for a very long time. Exploit Sales and Government Corruption, or Corporate Corruption, are the same thing. Malware and Government Corruption are the same thing. Both Actions exploit the system for profit, just like wall street and the major banks do. Zero Days is just another vulnerability in a world that has thousands of vulnerabilities. And knowledge is our best defense against ignorance, and vulnerabilities.
Human Rights
"The spying is not all about National Security, or even Malicious Greed, the Spying that is the most disturbing is the spying related to Paranoia. So you have to ask the question, what are they paranoid about? Why do they feel weak and insecure? You got caught with your hands in the cookie jar, but there's no cookie jar. You know how manipulating and dangerous misinformation can be, but can they tell when it's their own misinformation? When you're asking the wrong questions, you will never find the answers that you're hoping to find, so why continue to ask the wrong questions? You're wasting precious time Lord of the Flies. The only way this will work, is when we work together.
Whistle Blowing - Hero's who Blow the Whistle on Corrupt Activity
 Whistleblower is a person who
exposes any kind of information or
activity that is deemed illegal, unethical, or not correct within an
organization that is either private or public. Blowing the whistle is Not
the Same thing as leaking information
or being a backstabber.
Whistleblower is a person who
exposes any kind of information or
activity that is deemed illegal, unethical, or not correct within an
organization that is either private or public. Blowing the whistle is Not
the Same thing as leaking information
or being a backstabber.Public Interest Defense allows a defendant who disclosed classified or protected information to avoid criminality by establishing that the public interest in disclosure of the information outweighs the public interest in nondisclosure. It is aimed at protecting whistleblowers of government misconduct. Non-Disclosure Agreements being used to protect criminals.
Good Samaritan Law offers legal protection to people who give reasonable assistance to those who are, or who they believe to be, injured, ill, in peril, or otherwise incapacitated. The protection is intended to reduce bystanders' hesitation to assist, for fear of being sued or prosecuted for unintentional injury or wrongful death. Duty to Rescue - Watch Dogs.
False Claims Act is an American federal law that imposes liability on persons and companies (typically federal contractors) who defraud governmental programs. It is the federal Government's primary litigation tool in combating fraud against the Government. The law includes a qui tam provision that allows people who are not affiliated with the government, called "relators" under the law, to file actions on behalf of the government (informally called "whistleblowing" especially when the relator is employed by the organization accused in the suit). Persons filing under the Act stand to receive a portion (usually about 15–25 percent) of any recovered damages. As of 2012, over 70 percent of all federal Government FCA actions were initiated by whistleblowers. Claims under the law have typically involved health care, military, or other government spending programs, and dominate the list of largest pharmaceutical settlements. The government recovered $38.9 billion under the False Claims Act between 1987 and 2013 and of this amount, $27.2 billion or 70% was from qui tam cases brought by relators.
Witness Immunity is when a prosecutor grants immunity to a witness in exchange for testimony or production of other evidence. Above the Law?
Witness Protection Program is designed to protect threatened witnesses before, during, and after a trial.
Informant is a person who provides privileged information about a person or organization to an agency. Source.
Turn State's Evidence is for an accused or convicted criminal to testify as a witness for the state against his associates or accomplices. Turning state's evidence is occasionally a result of a change of heart or feelings of guilt, but is more often in response to a generous offer from the prosecution, such as a reduced sentence or a favorable location for serving time. In particularly high-profile or dangerous cases such as organized crime trials and other federal crimes trials, witnesses may be offered immunity from prosecution even if they have committed serious crimes themselves, sometimes even murder. The state may also offer the witness a place in the witness protection program, giving them a new identity, so they need not fear retaliation from their former accomplices. Corruption in the Justice System (bad judges and lawyers).
List of Whistleblowers (wiki) - Famous Infamous Whistleblowers
Russ Tice (wiki) - Thomas Andrews Drake (wiki)
Daniel Ellsberg (wiki) - Edward Snowden (wiki)
Julian Assange (wiki) - Wiki Leaks - Aaron Swartz (wiki)
5 New Whistleblowers Speak on Exposing Corruption Since Snowden (video)
War on Whistleblowers (ft. Edward Snowden & David Carr) 2015 (youtube)
Gary Webb was an American investigative journalist who is best known for his "Dark Alliance" series, which appeared in The Mercury News in 1996. The series examined the origins of the crack cocaine trade in Los Angeles and claimed that members of the anti-communist Contra rebels in Nicaragua had played a major role in creating the trade, using cocaine profits to support their struggle. It also suggested that the Contras may have acted with the knowledge and protection of the Central Intelligence Agency (CIA). The series provoked outrage, particularly in the Los Angeles African-American community, and led to four major investigations of its charges. (Gary Webb - August 31, 1955 – December 10, 2004).
CIA and Contras Cocaine Trafficking in the US (wiki)
Allegations of CIA Drug Trafficking (wiki) - Drug War
Iran-Contra Affair is when Senior Reagan Administration officials secretly facilitated the sale of arms to the Khomeini government of the Islamic Republic of Iran, which was the subject of an arms embargo. The administration hoped to use the proceeds of the arms sale to fund the Contras in Nicaragua. Under the Boland Amendment, further funding of the Contras by the government had been prohibited by Congress.
Philip Agee was a Central Intelligence Agency (CIA) case officer and writer, best known as author of the 1975 book, Inside the Company: CIA Diary, detailing his experiences in the CIA. Agee joined the CIA in 1957, and over the following decade had postings in Washington, D.C., Ecuador, Uruguay and Mexico. After resigning from the Agency in 1968, he became a leading opponent of CIA practices. A co-founder of CovertAction Quarterly, which was an American publication focused on and critical of the US Central Intelligence Agency. Covert Action relaunched in May 2018 as Covert Action Magazine. Philip died in Cuba in January 2008.
Activism - Activists - Journalism Hero's
Whistle blowing can be misused by the media to spread propaganda. Just like when the media calls something a conspiracy theory when in fact its just more propaganda or a tactic to silence a real whistle blower.
Reporting to police that you were raped is kind of like whistle blowing. It carries similar risks. Reporting a crime should not be risky or dangerous and should not ruin your life.
If you See Something, Say Something
If you know something, then say something. If you don't know something, then learn something. Just because you see something, this does not mean that you know something. Know what you see and see what you know.
Whistleblower Protection Act is a United States federal law that protects federal whistleblowers who work for the government and report the possible existence of an activity constituting a violation of law, rules, or regulations, or mismanagement, gross waste of funds, abuse of authority or a substantial and specific danger to public health and safety. A federal agency violates the Whistleblower Protection Act if agency authorities take (or threaten to take) retaliatory personnel action against any employee or applicant because of disclosure of information by that employee or applicant.
Whistleblowers Protection Program - Whistleblower Rights (PDF)
Whistle Blowers Center - Whistleblower
Freedom of the Press - Freedom of Speech
Government Watchdogs - Key Words
Expose Facts - I Paid a Bribe - The Intercept
Pentagon Papers (wiki) - National Security Archive (wiki)
Workplace Fairness
Congress 1998
"Sometimes Hero's Reap Rewards that were never intended for them, and other times the rewards are not even rewards at all."
Implicated - Legal Terms - Conformity Dangers
You are not a rat or a snitch or a tattletale when you report a crime, but that's not how criminals see it. Reporting a crime has its risks. That's because criminals can act like they are above the law, especially when the law doesn't act. The justice system does not work the way it should. When women are raped, police don't always investigate the crime. And when you report a white collar crime, there is no guarantee that the justice system will seek justice. And on top of that, you have to deal with retaliations and threats that comes from reporting a crime. So instead of being a hero, you're the one who ends up getting treated like a criminal. The justice system does not work the way it should. We know that the justice system does seek justice, it's just that it's not for everyone or all the time. Sometimes they even seek justice against innocent people. So in order to get justice you have to know someone on the inside of the justice system. If you want justice, you have to know the politics of the system and know how to negotiation and communicate. If you really want justice you have to do a lot of the work yourself, which millions of people have done and still do. This is not saying to take justice into your own hands, it's just saying that you should at least be in the car, even if you can't totally steer it. People need to educate themselves and be proactive and stand up for what is right. Every luxury and every freedom that people have today is from people acting and standing up for what is right. If people did not act, there would be no human life. So standing up is not just every citizens responsibility, it is a privilege and an honor to even have the chance.
When you hear someone talk about fraud, theft, or corruption that they have witnessed, that is a cry for help. And people need to respond, because we cannot always be reliant on a justice system that is corrupt itself, if we don't act who will? If you have a chance to correct flaws and mistakes, you should. Even if your search for justice or change comes up short, we can still benefit from that experience of seeking change. Things that you learn can be used towards other methods of communication. Things that you learn can also be used to correct other injustices, now and in the future. Sadly we don't even have one trusted source for information, there's not one source for trusted information, how can that be? Communication is our greatest strength. Collectively our power is limitless, but when we can't communicate effectively, we lose a tremendous amount of power, wealth and potential. And these are the things that all humans seek, but the problem is that we have not yet figured out how to correct our communication flaws. Our ability to transfer knowledge using language is a gift, we should not take this ability for granted. Communication is a power that everyone can share and benefit from. Lawsuits.
Nothing to Hide
Every person on the planet has things about themselves that they would like to keep private, especially knowing that things can be misinterpreted or used maliciously. You have nothing to worry about just as long as you think that you're not doing anything wrong is an ignorant belief and misleading assumption. It's not 'if ' you're doing anything wrong, it's knowing that anything that you say or do can be used against you, either to manipulate you or to exploit you, and 90% of people will never know that they've been victimized. So don't be a fool. Privacy is like freedom, if you don't protect your privacy, then you don't have privacy. And if you don't protect your freedom, then you don't have freedom. Welcome to reality. NOTHING TO HIDE documentary (Eng, 2017) (youtube). Mobile Phone Eavesdropping.
What if you were having a private conversation with someone and then some total stranger came and stood next to you? You would either move away from the total stranger, or you would stop talking about anything personal. But what if a stranger was invisible and did not know that someone was listening? You have nothing to hide until someone uses your personal information to manipulate you without you even knowing it. Information can also be used to slander you or blackmail you. Then the only thing that you were hiding was your naive ignorance. Not only did you selfishly think of just yourself and your own perceived lack of vulnerabilities, your were not thinking about your family, your friends, or other peoples vulnerabilities. One weak link in a chain can break the chain. Just like with herd immunity. One infected person can do a lot of damage. Intellectual Freedom.
Even when people here about famous peoples privacy invasion, people still don't get it. How would you like it if a total stranger came up to you and pretended to know you just because they have access to some of your personal information. They know nothing about you, other than their personal interpretation of some details about you. Usually if someone accuses you of a crime, they have to produce evidence and witnesses, and also convince 12 jurors to see what they believe they see, like a Ponzi scam. Cherry Picking Data.
Who is Who? Who's asking and what for? Labels and profiles can be misused and abused, especially by people who have criminal intent. When we were kids in the early 70's we would scare our friends and say as a joke that "The FBI has a File on you". Then everyone forgot about this type of privacy intrusion and suffered mass amnesia, so here we are again.
 If you have nothing to hide then you have nothing to worry about.
Most all of us have friends that we can
trust and feel comfortable with, friends who we don't mind
sharing our personal thoughts or secrets with. But what if you had a
friend who was a deviate criminal who couldn't be trusted? A
person who wouldn't mind sharing your personal information or
secrets with other people in order to
manipulate them. Then you would most likely not share any
personal information with that person. So the real question is,
what if that deviate criminal was able to spy on you and
document almost every move
that you make or every word you speak?
That would suck because you would be
always worrying about what
information and knowledge could be
exploited and used against you, or, used against some other
innocent people. Nothing to hide is one thing, something that
can be misconstrued is another, after all, we're talking about
criminals. So I would not want you to be too complacent about
the possible dangers and scams that are on the Internet or any
where else. So please educate yourself, and if you are concerned
about something then please get as many opinions as you can, and
always ask for help from a well trusted source.
If you have nothing to hide then you have nothing to worry about.
Most all of us have friends that we can
trust and feel comfortable with, friends who we don't mind
sharing our personal thoughts or secrets with. But what if you had a
friend who was a deviate criminal who couldn't be trusted? A
person who wouldn't mind sharing your personal information or
secrets with other people in order to
manipulate them. Then you would most likely not share any
personal information with that person. So the real question is,
what if that deviate criminal was able to spy on you and
document almost every move
that you make or every word you speak?
That would suck because you would be
always worrying about what
information and knowledge could be
exploited and used against you, or, used against some other
innocent people. Nothing to hide is one thing, something that
can be misconstrued is another, after all, we're talking about
criminals. So I would not want you to be too complacent about
the possible dangers and scams that are on the Internet or any
where else. So please educate yourself, and if you are concerned
about something then please get as many opinions as you can, and
always ask for help from a well trusted source.
I have nothing to hide so I why should I worry? Which actually means that you have nothing to hide because you have nothing between your ears. So yes, you have nothing to hide except your own ignorance. Maybe you have nothing to hide because you have nothing of value to add to society, or that you just don't care about the victims of crimes or the vulnerabilities of our society. Hiding this shame is easy when you're ignorant.
Privacy is also about being protected from criminals. Protection from peeping toms, protection from slander, protection from unlawful search and seizures, protection from unfair competition and unfair monopolies, protection from unfair regulations and laws. I want to do what is right and good for everyone, and not just do what is perceived to be right and good for some criminal corporation or for some corrupt state or government. Everyone is supposed to be innocent until proven guilty, and not be guilty just because some corrupt organization believes that your not innocent.
Voyeurism is spying on people engaged in intimate behaviors, such as undressing, sexual activity, or other actions usually considered to be of a private nature.
There is no such thing as Nothing, because nothing doesn't exist, there's always something. A person can see you acting weird and then ask you "what's wrong?" And then you say "Nothing", which is a lie. There is something wrong with you and you may be to embarrassed to say what's wrong with you or that you have no idea what's wrong with you. So all you can say is "I don't know what's wrong or that you would rather not say what's wrong." Space is never empty.
The law-abiding citizens have nothing to fear from government surveillance... unless the government begins to break the law.
You don't have to worry about your personal information being exploited by normal and respectable people, because those people don't care about your personal information, unless that information provided something of value to society, in that case they would just ask for your consent. The real danger is criminals, and those criminals can be from your government, your businesses, your associates, or any one involved with criminal activities. So you have nothing to worry about except criminals. And knowing who exactly the criminals are is not easy, but not impossible. People should be Paid for their Information.
Teaching the public extensively about how and where personal information can be exploited can greatly increase their protection. Criminals and persons that are steeling and manipulating personal information are everywhere, in almost every type of business, legal and illegal. So start educating the young about how this morally destructive behavior, which in most cases are fueled by greed and power, is wrong on so many levels that it not just threatens our character, but our survival. Though the freedom to information is highly essential to our growth, we must know that criminal minds are not going away anytime soon. So back up your data and secure it with a trusted friend or relative. It’s not just about your personal information falling into the wrong hands, it’s more about your personal information never being found when needed.
Information Brokers or Data Brokers have information on you that's similar to your Personal FBI Files. Your Personal Dossier Profile can have over 1,500 separate pieces of information: Political Views, Voting History, Medical History, Psychiatric Problems, Religion, Friends Names, Family Names, Race, Income, Credit Report, Bank Accounts, SS #'s, Credit Card #'s, Properties owned, Cars, Weapons, Police Reports, Drug Problems, Driving Record, Lawsuits, Jobs you had, Sexual Orientation, Restaurants, Items Purchased, Websites you visited over the years, Search Words you used, Geo-Location Data from Cell Phones, and so on and so on. This Information is mostly used by scumbag marketing advertisers who ignorantly believe that they are actually necessary, not even close. You are a defect in the system that lives off another defect in the system, none of which benefits people in the ways it should.
Epsilon - Acxiom - Dataium - Lotame - Spokeo
The word 'Hacker' is just another stereotyping keyword that the media uses to manipulate and distract the public from the facts. A Hacker is just someone who has a unique set of computer skills and knowledge, which does not make them a criminal. When someone uses advanced knowledge to commit a crime that does not make having that knowledge a crime, it only suggests that someone committed a crime, which still needs to be determined in a court of law, a court of law that is not corrupt or manipulated. Corporations and Governments are involved in criminal activities everyday. Committing the same crimes that so called Hackers commit. And corporations and governments are much more destructive and dangerous to society then any hacker or terrorist could ever dream of being. So don't allow yourself to be distracted.
Anonymity - You Don't Need to Know My Name
People need Anonymity, but not to hide deviate behavior, but to protect themselves from idiots and criminals.
Anonymity is being anonymous and being non-identifiable, unreachable, untrackable and untraceable. Anonymity is seen as a technique, or a way of realizing, certain other values, such as privacy, or liberty. Anonymity means "without a name" or "namelessness". Proxy Server - TOR Browser - VPN.
Anonymous is someone or something not known or lacking marked individuality. Nameless. Being or having an unknown or unnamed source. Anonymous - Guy Fawkes Mask.
Inconspicuous is someone or something not prominent or readily noticeable, Not drawing attention.
Privacy is the ability of an individual or group to seclude themselves, or information about themselves, and thereby express themselves selectively. The boundaries and content of what is considered private differ among cultures and individuals, but share common themes. When something is private to a person, it usually means that something is inherently special or sensitive to them. The domain of privacy partially overlaps security and confidentiality, which can include the concepts of appropriate use, as well as protection of information. Privacy may also take the form of bodily integrity. The right not to be subjected to unsanctioned invasions of privacy by the government, corporations or individuals is part of many countries' privacy laws, and in some cases, constitutions. In the business world, a person may volunteer personal details, including for advertising, in order to receive some sort of benefit. Public figures may be subject to rules on the public interest. Personal information which is voluntarily shared but subsequently stolen or misused can lead to identity theft. The concept of universal individual privacy is a modern construct primarily associated with Western culture, British and North American in particular, and remained virtually unknown in some cultures until recent times. Most cultures, however, recognize the ability of individuals to withhold certain parts of their personal information from wider society, such as closing the door to one's home. Not to be Confused with Secrecy, which is people hiding criminal activity. Being Popular or Famous.
Right to Privacy is to restrain governmental and private actions that threaten the privacy of individuals. Search Warrant.
Laws Protecting Privacy - Invasion of Privacy is a tort based in common law allowing an aggrieved party to bring a lawsuit against an individual who unlawfully intrudes into his/her private affairs, discloses his/her private information, publicizes him/her in a false light, or appropriates his/her name for personal gain. Invasion of privacy is the intrusion into the personal life of another person without consent. However, invasion of privacy is not the cause of action or tort that you would sue another person. For these reasons, it's important to check your state's laws or consult with a local attorney before filing a lawsuit. False Light is similar to a defamation claim in that it allows an individual to sue for the public disclosure of information that is misleading (or puts that person in a "false light"). The right of privacy is: the right of a person to be free from unwarranted publicity, the unwarranted appropriation or exploitation of one’s personality, the publicizing of one’s private affairs with which the public has no legitimate concern, or the wrongful intrusion into one’s private activities in such manner as to outrage or cause mental suffering, shame or humiliation to a person of ordinary sensibilities. The right of privacy has two main aspects: the general law of privacy, which affords a tort action for damages resulting from an unlawful invasion of privacy; and
the constitutional right of privacy which protects personal privacy against unlawful governmental invasion.In an action for recovering damages for a privacy right violation, a plaintiff must allege the following elements: that there was an unwarranted invasion of individual privacy; that there was an intentional intrusion on his/her private concerns; that publication was without plaintiff’s written consent, where written consent is required; and that plaintiff’s name or picture was used for trade or advertising purposes, where privacy invasion is alleged by publication of one’s name or likeness for trade and advertising purposes.
“right to be left alone”. Privacy Laws allow an aggrieved party to bring a lawsuit against an individual who unlawfully intrudes into their private affairs, discloses their private information, publicizes them in a false light, or appropriates their name for personal gain.
Your Data can still be Identified even if it’s Anonymized. Urban planners and researchers at MIT found that it’s shockingly easy to “reidentify” the anonymous data that people generate all day, every day in cities.
Concealment - Shielded is to protect, hide, or conceal from danger or harm. Protected. Kept safe or defended from danger or injury or loss. Camouflage.
Window Film or Tinted Windows are used for heat and glare reduction, thermal insulation, UV filtration, safety and security, privacy, decoration, signage and branding and protection from graffiti.
Discretion is the freedom to act or judge on one's own. Knowing how to avoid embarrassment or distress. The power of making free choices unconstrained by external agencies. The trait of judging wisely and objectively.
You can use a Disposable Identity or Fake Identity if you feel the need.
Fake Your Identity Online (wiki how) - Identity Forgery (wiki)
Privacy Tools - Safe Browsing on the Internet
Your Digital Identity has Three Layers, and you can only protect one of them. The first layer is your profile information, your public posts and private messages, likes, search queries, uploaded photos, tests and surveys you took, events you attended, websites you visited, and other types of conscious interactions. The second layer is made of behavioral observations. These are not so much choices you consciously make, but the metadata that gives context to those choices. It contains things that you probably do not want to share with everybody, like your real-time location and a detailed understanding of your intimate and professional relationships. (By looking at location patterns that reveal devices that often meet in the same office buildings or “sleep” together in the same houses, tech companies can tell a lot about who you spend your time with.) It also tracks your patterns of when you’re online and offline, content you clicked on, time you spent reading it, shopping patterns, keystroke dynamics, typing speed, and movements of your fingers on the screen (which some companies believe reveal emotions and various psychological features). The third layer is composed of interpretations of the first and second. Your data are analyzed by various algorithms and compared with other users’ data for meaningful statistical correlations. This layer infers conclusions about not just what we do but who we are based on our behavior and metadata. It is much more difficult to control this layer, as although you can control the inputs (posting photos of your newborn), you don’t know the algorithm that is spitting the output (that you might need to order nappies). The task of these profile-mapping algorithms is to guess things that you are not likely to willingly reveal. These include your weaknesses, psychometric profile, IQ level, family situation, addictions, illnesses, whether we are about to separate or enter in a new relationship, your little obsessions (like gaming), and your serious commitments (like business projects). When your Data Double is Wrong. The troubling thing is that we as users might not like or recognize ourselves in the profiles that are created for us. How would it feel if you discovered your “data double” is sick or emotionally unstable, not credit worthy, or not simply not cool enough, all because of the way you type, your search queries, or any “strange” relationships you may have? People should be Paid for their Information.
Tor Anonymity Network is free and open-source software for enabling anonymous communication. The name is derived from an acronym for the original software project name "The Onion Router". Tor directs Internet traffic through a free, worldwide, volunteer overlay network consisting of more than seven thousand relays to conceal a user's location and usage from anyone conducting network surveillance or traffic analysis. Using Tor makes it more difficult to trace Internet activity to the user: this includes "visits to Web sites, online posts, instant messages, and other communication forms". Tor's intended use is to protect the personal privacy of its users, as well as their freedom and ability to conduct confidential communication by keeping their Internet activities unmonitored. Tor does not prevent an online service from determining when it is being accessed through Tor. Tor protects a user's privacy, but does not hide the fact that someone is using Tor. Some websites restrict allowances through Tor. For example, Wikipedia blocks attempts by Tor users to edit articles unless special permission is sought. Onion routing is implemented by encryption in the application layer of a communication protocol stack, nested like the layers of an onion. Tor encrypts the data, including the next node destination IP address, multiple times and sends it through a virtual circuit comprising successive, random-selection Tor relays. Each relay decrypts a layer of encryption to reveal the next relay in the circuit to pass the remaining encrypted data on to it. The final relay decrypts the innermost layer of encryption and sends the original data to its destination without revealing or knowing the source IP address. Because the routing of the communication was partly concealed at every hop in the Tor circuit, this method eliminates any single point at which the communicating peers can be determined through network surveillance that relies upon knowing its source and destination. An adversary may try to de-anonymize the user by some means. One way this may be achieved is by exploiting vulnerable software on the user's computer. The NSA had a technique that targets a vulnerability – which they codenamed "EgotisticalGiraffe" – in an outdated Firefox browser version at one time bundled with the Tor package and, in general, targets Tor users for close monitoring under its XKeyscore program. Attacks against Tor are an active area of academic research which is welcomed by the Tor Project itself. The bulk of the funding for Tor's development has come from the federal government of the United States, initially through the Office of Naval Research and DARPA. Safe Browsing.
Onion Routing is a technique for anonymous communication over a computer network. In an onion network, messages are encapsulated in layers of encryption, analogous to layers of an onion. The encrypted data is transmitted through a series of network nodes called onion routers, each of which "peels" away a single layer, uncovering the data's next destination. When the final layer is decrypted, the message arrives at its destination. The sender remains anonymous because each intermediary knows only the location of the immediately preceding and following nodes. There are methods to break the anonymity of this technique, e.g. timing analysis. Utilising timing analysis, the anonymity of TORs can be broken. One of the reasons typical Internet connections are not considered anonymous, is the ability of Internet service providers to trace and log connections between computers. For example, when a person accesses a particular website, the data itself may be secured through a connection like HTTPS such that the user's password, emails, or other content is not visible to an outside party, but there is a record of the connection itself, what time it occurred, and the amount of data transferred. Onion routing creates and obscures a path between two computers such that there's no discernible connection directly from a person to a website, but there still exist records of connections between computers. Traffic analysis searches those records of connections made by a potential originator and tries to match timing and data transfers to connections made to a potential recipient. For instance, one can change the timings of the packets of a flow according to a specific pattern and look for that pattern on the other side of the network. Also, a person may be seen to have transferred exactly 51 kilobytes of data to an unknown computer just three seconds before a different unknown computer transferred exactly 51 kilobytes of data to a particular website. Factors that may facilitate traffic analysis include nodes failing or leaving the network and a compromised node keeping track of a session as it occurs when chains are periodically rebuilt. Garlic Routing is a variant of onion routing associated with the I2P network that encrypts multiple messages together to make it more difficult for attackers to perform traffic analysis and to increase the speed of data transfer. Exit node vulnerability. Although the message being sent is transmitted inside several layers of encryption, the job of the exit node, as the final node in the chain, is to decrypt the final layer and deliver the message to the recipient. A compromised exit node is thus able to acquire the raw data being transmitted, potentially including passwords, private messages, bank account numbers, and other forms of personal information. Dan Egerstad, a Swedish researcher, used such an attack to collect the passwords of over 100 email accounts related to foreign embassies. Exit node vulnerabilities are similar to those on unsecured wireless networks, where the data being transmitted by a user on the network may be intercepted by another user or by the router operator. Both issues are solved by using a secure end-to-end connection.
Public-key Cryptography is a cryptographic system that uses pairs of keys: public keys which may be disseminated widely, and private keys which are known only to the owner. The generation of such keys depends on cryptographic algorithms based on mathematical problems to produce one-way functions. Effective security only requires keeping the private key private; the public key can be openly distributed without compromising security. In such a system, any person can encrypt a message using the receiver's public key, but that encrypted message can only be decrypted with the receiver's private key. Robust authentication is also possible. A sender can combine a message with a private key to create a short digital signature on the message. Anyone with the corresponding public key can combine a message, a putative digital signature on it, and the known public key to verify whether the signature was valid, i.e. made by the owner of the corresponding private key. Public key algorithms are fundamental security ingredients in modern cryptosystems, applications and protocols assuring the confidentiality, authenticity and non-repudiability of electronic communications and data storage. They underpin various Internet standards, such as Transport Layer Security (TLS), S/MIME, PGP, and GPG. Some public key algorithms provide key distribution and secrecy (e.g., Diffie–Hellman key exchange), some provide digital signatures (e.g., Digital Signature Algorithm), and some provide both (e.g., RSA).
PC Threats - Vulnerabilities - Protection Tools
Vulnerability in computing is a weakness which allows an attacker to reduce a system's information assurance. Vulnerability is the intersection of three elements: a system susceptibility or flaw, attacker access to the flaw, and attacker capability to exploit the flaw. To exploit a vulnerability, an attacker must have at least one applicable tool or technique that can connect to a system weakness. In this frame, vulnerability is also known as the attack surface.
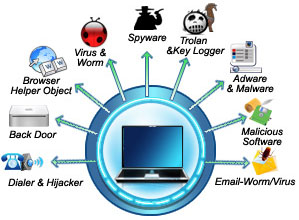
"Making sure that the virus protection doesn't turn into a virus itself"
Nothing to Hide - Privacy - Safe Surfing - Anonymity - Data Protection
Keep your Operating System updated To avoid Threats & Vulnerabilities.
PC Problem Solving
Banking Online: If you do online banking: If you use your bank account to send and receive money make sure it is not linked to any other bank accounts that you have. This way you can keep the minimal money needed in your online account so that you do not risk having all your money being stolen. When typing in personal information make sure you see the 'S' after the http ( https:// ) in the browser address bar. S stands for SSL certificate which is short for Secure Sockets Layer. You should see this when putting in personal information like credit card numbers, social security numbers and passwords. The SSL help protects you from hackers seeing what you are typing because what you type is Encrypted. But still this does not guarantee that your information is safe because of other vulnerabilities like hackers, key stroke recorders, viruses and fake websites.
A Video about how your personal information is being sold - Dispatches - The Data Theft Scandal (video)
Big Brother Big Business another film about Data Mining and the information War (video)
Credit Cards: If you use a credit card for online purchases: Please have a low credit limit and try to use only one credit card on the internet. So if that credit card information is stolen thieves will not be able to make any big charges on your credit card. If you do need to increase your credit limit to buy something expensive, then you can call your credit card provider to increase your credit limit. This will also keep you from doing any impulse purchases because you now have to make a phone call first to ask for the credit increase.
Warning: If you have good credit and you are financially secure you must take extra steps in order to secure your personal information and finances. One step is to put a freeze on new accounts being open so that thieves are not able to get credit cards in your name.
ID Theft Affidavit (FTC) - Identity Theft - Monitoring Credit Scores
Money Management Education
Track your Laptop, Cell Phone and Tablet whenever stolen or missing: Open source software with full and remote control, 24/7 - Tracking Devices.
Browsers - Safe Internet Surfing
Temporary Internet files, Cookies, Virus Protection and Browser Settings: It's a good idea to delete your temporary internet files as well as your Cookies, especially knowing that some tracking cookies record every website you visit. This way advertisers can manipulate what adds you see on websites, manipulate what websites you see in your internet searches and also know what kind of spam e-mails to send you. They can also sell this information to others. The Wall Street Journal measured 50 of the most popular websites and found that they installed a total of 3,180 tracking files on a test computer. This is very annoying and intrusive but there are ways to minimize these types of attacks on your privacy. Each browser has a different way of clearing these files and cookies so please learn how to do this yourself so that you can do it once a month. At the top of your browser window look for 'Tools' and then 'Options' and learn how to adjust your security settings (Like Private Browsing, Note: Certain privacy browser settings 'Like Private Browsing' and not allowing cookies can cause some of your usernames & passwords from working). Before you clear the passwords from your browser make sure you write each one down incase you need to retype them in later. Always have at least 2 internet browsers on your PC incase one does not work or gets infected.
Privacy Choice - ULR Query
Private Browsing gets more Private. New system patches security holes left open by web browsers’ private-browsing functions. System uses JavaScript decryption algorithms embedded in web pages and code obfuscation to patch security holes left open by web browsers' private-browsing functions.
Tor (safe browsing)
Internet Browsers for Kids
Mozilla Firefox Lightbeam (see who's tracking you online) - Lightbeam
Disconnect.me (stop online advertiser tracking)
Cookies (tracking and profiling)
Browser Usage Stats
Usage Share of Web Browsers
Avecto: Windows Vulnerabilities
Internet Searching Tips - Internet Access Tools
Browsers for the Internet that are Free: Mozilla Firefox - Chrome - Opera - Apple Safari - Hatdex RUMPEL Web Browser
Web Browser is one of the most efficient and effective tools for navigating through information.
Anansi Browser is a lightweight Windows utility designed to help users navigate on the Internet in a clean and intuitive working environment.
Computer Viruses - Computer Vulnerabilities
 Computer Virus
is a type of malicious software program ("malware") that, when executed,
replicates by reproducing itself (copying its own source code) or
infecting other computer programs by modifying them. Infecting computer
programs can include as well, data files, or the "boot" sector of the hard
drive. When this replication succeeds, the affected areas are then said to
be "infected" with a computer virus.
Computer Virus
is a type of malicious software program ("malware") that, when executed,
replicates by reproducing itself (copying its own source code) or
infecting other computer programs by modifying them. Infecting computer
programs can include as well, data files, or the "boot" sector of the hard
drive. When this replication succeeds, the affected areas are then said to
be "infected" with a computer virus. System Restore - Reboot Computer
Malware is any software used to disrupt computer or mobile operations, gather sensitive information, gain access to private computer systems, or display unwanted advertising. Stuxnet Malware.
Spyware is software that aims to gather information about a person or organization without their knowledge, that may send such information to another entity without the consumer's consent, or that asserts control over a device without the consumer's knowledge.
Keystroke Logging is the action of recording (logging) the keys struck on a keyboard, typically covertly, so that the person using the keyboard is unaware that their actions are being monitored.
Keystroke Dynamics is the detailed timing information which describes exactly when each key was pressed and when it was released as a person is typing at a computer keyboard.
Computer Worm is a standalone malware computer program that replicates itself in order to spread to other computers. Often, it uses a computer network to spread itself, relying on security failures on the target computer to access it. Worms almost always cause at least some harm to the network, even if only by consuming bandwidth, whereas viruses almost always corrupt or modify files on a targeted computer.
Backdoor in computing is a typically covert method of bypassing normal authentication or encryption in a computer, to gain remote access to a computer. Any computer product, embedded device (e.g. a home router), or its embodiment (e.g. part of a cryptosystem, algorithm, chipset, or even a "homunculus computer" —a tiny computer-within-a-computer such as that found in Intel's AMT technology), can be taken over. Backdoors are most often used for securing remote access to a computer, or obtaining access to plaintext in cryptographic systems. From there it may be used to gain access to privileged information like passwords, corrupt or delete data on hard drives, or transfer information within autoschediastic networks. A backdoor may take the form of a hidden part of a program, a separate program (e.g. Back Orifice may subvert the system through a rootkit), code in the firmware of the hardware, or parts of an operating system such as Windows. Trojan horses can be used to create vulnerabilities in a device. A Trojan horse may appear to be an entirely legitimate program, but when executed, it triggers an activity that may install a backdoor. Although some are secretly installed, other backdoors are deliberate and widely known. These kinds of backdoors have "legitimate" uses such as providing the manufacturer with a way to restore user passwords. Many systems that store information within the cloud fail to create accurate security measures. If many systems are connected within the cloud, hackers can gain access to all other platforms through the most vulnerable system. Default passwords (or other default credentials) can function as backdoors if they are not changed by the user. Some debugging features can also act as backdoors if they are not removed in the release version. In 1993, the United States government attempted to deploy an encryption system, the Clipper chip, with an explicit backdoor for law enforcement and national security access. The chip was unsuccessful.
Trojan Horse in computing is any malware which misleads users of its true intent. The term is derived from the Ancient Greek story of the deceptive Trojan Horse that led to the fall of the city of Troy. Trojans may allow an attacker to access users' personal information such as banking information, passwords, or personal identity. It can also delete a user's files or infect other devices connected to the network. Ransomware attacks are often carried out using a Trojan. Unlike computer viruses and worms, Trojans generally do not attempt to inject themselves into other files or otherwise propagate themselves. For example, a user is duped into executing an e-mail attachment disguised to appear not suspicious, (e.g., a routine form to be filled in), or by clicking on some fake advertisement on social media or anywhere else.
Pwn is to compromise or control, specifically another computer (server or PC), website, gateway device, or application. It is synonymous with one of the definitions of hacking or cracking, including iOS jailbreaking. The Pwnie Awards are awarded by a group of security researchers.
Hacker (definitions) - Spying on the Scammers [Part 1/4] (youtube)
The Shadow Brokers is a hacker group originating in summer 2016. They published several leaks of some of the National Security Agency (NSA) hacking tools including zero-day exploits. Specifically, exploits and vulnerabilities targeting enterprise firewalls, anti-virus products and Microsoft products, tied to the Equation Group threat actor, NSA's Tailored Access Operations (TAO). DNS.
Ransomware Malware is computer malware that installs covertly on a victim's device (e.g., computer, smartphone, wearable device) and that either mounts the cryptoviral extortion attack from cryptovirology that holds the victim's data hostage, or mounts a cryptovirology leakware attack that threatens to publish the victim's data, until a ransom is paid.
Computer Fraud and Abuse Act was enacted by Congress in 1986 as an amendment to existing computer fraud law (18 U.S.C. § 1030), which had been included in the Comprehensive Crime Control Act of 1984.
Electronic Communications Privacy Act was enacted by the United States Congress to extend government restrictions on wire taps from telephone calls to include transmissions of electronic data by computer.
Storm Botnet is a remotely controlled network of "zombie" computers (or "botnet") that have been linked by the Storm Worm, a Trojan horse spread through e-mail spam.
Botnet is a number of Internet-connected devices used by a botnet owner to perform various tasks. Botnets can be used to perform Distributed Denial Of Service Attack, steal data, send spam, allow the attacker access to the device and its connection. The owner can control the botnet using command and control (C&C) software. The word botnet is a combination of the words robot and network. The term is usually used with a negative or malicious connotation.
Virus Protection
Keep your Virus Software Up to Date because that will also help protect your private information, though it is not a guarantee. 1 in 1,000 Websites are infected with Malicious Software. The moment you visit these infected websites malicious software or viruses are downloaded to your PC without you even knowing, so stay protected and be careful what you click on. The best virus protection is education.
Free Virus Protection - Spyware Protection Software - Security Essentials - Avira - AVG - Avast - Trend Micro
Computer Resources
Protect yourself from 15 Million Malicious Computer Programs
Lava Soft Ad-Ware - Spybot Search and Destroy - CCleaner - Malwarebytes - Hijack This - Spyware Blaster
Download.com has the software above.
Identify Programs Running on PC - Stop Badware
Be very careful not to click on the wrong download item. Please Verify the correct ".exe file."
ZMap is a free and open-source security scanner that was developed as a faster alternative to Nmap. ZMap was designed for information security research and can be used for both white hat and black hat purposes. The tool is able to discover vulnerabilities and their impact, and detect affected IoT devices. Using one gigabit per second of network bandwidth, ZMap can scan the entire IPv4 address space in 44 minutes on a single port.
ULR Query detecting and analyzing web-based malware. It provides detailed information about the activities a browser does while visiting a site and presents the information for further analysis.
Know when someone spies on you.
Tip: Make up fake answers to the most common security questions. Use a VPN or virtual private network. Routing your internet traffic through a middleman server.
Disk Encryption is a technology which protects information by converting it into unreadable code that cannot be deciphered easily by unauthorized people. Disk encryption uses disk encryption software or hardware to encrypt every bit of data that goes on a disk or disk volume. It is used to prevent unauthorized access to data storage.
Spam
Spamming is the use of electronic messaging systems to send an unsolicited message (spam) over and over again, especially advertising, as well as sending messages repeatedly on the same site. While the most widely recognized form of spam is email spam, the term is applied to similar abuses in other media: instant messaging spam, Usenet newsgroup spam, Web search engine spam, spam in blogs, wiki spam, online classified ads spam, mobile phone messaging spam, Internet forum spam, junk fax transmissions, social spam, spam mobile apps, television advertising and file sharing spam.
Email Spam also known as junk email, is a type of electronic spam where unsolicited messages are sent by email.
Email Marketing is the act of sending a commercial message, typically to a group of people, using email. Marketing Madness
Market Researchers say nearly 300 Billion e-mails are sent each day. Information Overload.
E-Mail Software to Help Control Spam - Spamato - Spam Bayes - Get pop file - Mail Washer - Sane Box - Google Priority-inbox Email Filter.
Anti-Spam Techniques are used to prevent email spam or unsolicited bulk email. Block specific email addresses.
Filtering Information - Propaganda - Clickbait
Grey Listing is a method of defending e-mail users against spam. A mail transfer agent (MTA) using greylisting will "temporarily reject" any email from a sender it does not recognize. If the mail is legitimate, the originating server will try again after a delay, and if sufficient time has elapsed, the email will be accepted. A server employing greylisting deliberately degrades mail service for unknown or suspect sources, over a short period of time. Typically, it records three pieces of data, known as a "triplet", for each incoming mail message: The IP address of the connecting host. The envelope sender address. The envelope recipient address(es), or just the first of them.
Junk Mail: Stop Junk Mail from your Mailman.
Unsolicited means not asked for, or given without being requested. Things that are unwelcome or uninvited. Like Rape, Sexual Harassment, junk mail and most of the things on the News.
Phone Calls - Stop Annoying Calls
Robocalls and spam phone calls have reached epidemic levels. Unwanted calls are by far the largest source of consumer complaints to the FTC, up to 7.1 million in 2017 versus 5.3 million in 2016. YouMail estimated that there were 3.4 billion robocalls placed in April of 2018, up from 2.5 billion in April of 2017. Phone-verification service Truecaller reports that while in 2014 the average American received 15 spam phone calls a month, by 2018 the average American was getting slammed with 23 spam phone calls a month. The Fix: Make it so every phone has a certificate of authenticity attached to it — a kind of digital signature — that allows you to once again trust your caller ID. The (greatly) simplified way this would work: Someone would place an outbound call. That call would contain a certificate verifying that the call is indeed coming from the number it claims to be coming from. The phone call is passed along to the incoming carrier (e.g., AT&T), which would then check the certificates public key against a heavily encrypted private key. A policy administrator, run by the telecom industry with oversight from the FCC, would be in charge of handing out certificates and making sure everything is on the level. Google.
Do not Call - Complaint Database
Robo Call is a phone call that uses a computerized autodialer to deliver a pre-recorded message, as if from a robot. Robocalls are often associated with political and telemarketing phone campaigns, but can also be used for public-service or emergency announcements. Some robocalls use personalized audio messages to simulate an actual personal phone call. Stop Robocalls.
Connecticut residents still getting around 470 million robo-calls in 2020 and U.S. telephone customers are bombarded with nearly 46 billion robocalls last year in 2020.
The Federal Trade Commission lists tips on how to block unwanted calls.
Youmail has an app for cellphones to reduce robocalls.
Reverse Phone Number Lookup - Call Them All
Robocalls: Last Week Tonight with John Oliver (HBO) (youtube)
Mass Calling System Delivers phone messages to thousands of call recipients at once.
Caller ID Spoofing is when caller ID displays a different number or a fake number and name of the caller so as to trick you into answering the phone call. A criminal is hacking the telephone network to indicate to the receiver of a call that the originator of the call is a station other than the true originating station. For example, a caller ID display might display a phone number different from that of the telephone from which the call was placed. The term is commonly used to describe situations in which the motivation is considered malicious by the originator. What if someone knocks on your door and pretends to be someone else?
Impersonation is an act of falsely portraying oneself as a member of an organization or institution, for the purpose of deception. In the vast majority of countries, the practice is illegal and carries a custodial sentence. Actor - Front Group.
Home Invasion is an illegal and usually forceful entry to an occupied, private dwelling with intent to commit a violent crime against the occupants, such as robbery, assault, rape, murder, or kidnapping. False Advertising.
Identity Fraud is the use by one person of another person's personal information, without authorization, to commit a crime or to deceive or defraud that other person or a third person.
Marketing Madness Hang-up when you are talking, this way they will think that you were cut off and lost connection.
Telemarketing is a method of direct marketing in which a salesperson solicits prospective customers to buy products or services, either over the phone or through a subsequent face to face or Web conferencing appointment scheduled during the call. Telemarketing can also include recorded sales pitches programmed to be played over the phone via automatic dialing.
Auto Dialer is an electronic device or software that automatically dials telephone numbers. Once the call has been answered, the autodialer either plays a recorded message or connects the call to a live person.
SIM-Swap Scams Expose Risks Of Using Phones For Secondary I.D. SIM-swap is a "social engineering" trick fraudsters use to take control of somebody else's phone number. A type of account takeover fraud that generally targets a weakness in two-factor authentication and two-step verification in which the second factor or step is a text message (SMS) or call placed to a mobile telephone. There are a couple of ways to do this. Sometimes they'll fool the phone company into believing they're the number's rightful owner, who lost the phone and needs to transfer service to a new device. And sometimes it's an inside job, with phone company staffers helping to make the switch, as alleged by federal prosecutors in a case this spring. Once scammers control your number, they can get your text messages — including the verification codes many online services send when customers reset their passwords. These are different from verification codes generated by two-factor apps or hardware keys, which are more secure because they don't depend on a phone number. But companies often use the text-message version because it's simple to use. Scammers used text-message verification codes to get into email accounts, and from there it is open season. The big prize can be a Bitcoin account. It's not clear exactly how they used his phone number to log in, but once they did, they can steal Bitcoin. People who are using phones as their only source of two-factor identification are inviting identity theft.
Get a Human Direct Company Phone Numbers without Menu.
Don't forget, before you hang up the phone, make this request below, by law they have to remove you from the call list.....
Please Put Me On Your Do Not Call List..or put me me on the do not waste my f*cking time list, especially if you are just wasting valuable time, energy, resources, people and money.
